OSPF Authentication Explained and Configuration on Nexus switches
We want to configure authentication on OSPFv2 messages to prevent unauthorized or invalid routing updates
For OSPF Authentication, we have mainly 2 options:
- Simple password authentication
- MD5 authentication digest (preferred)
Lab topology:
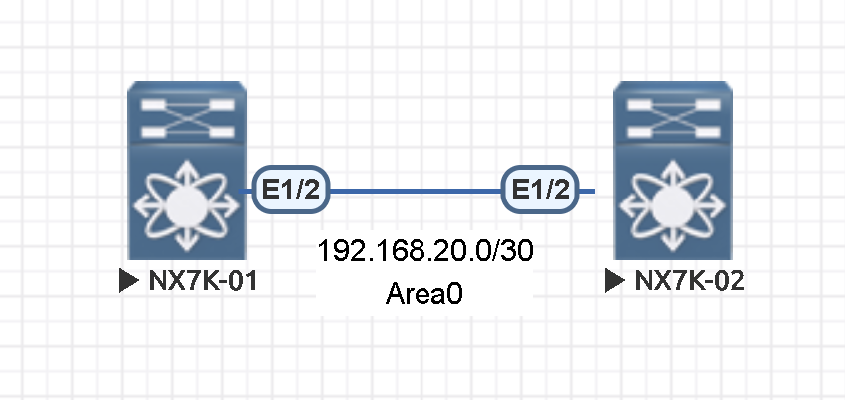
Simple password Authentication
uses a simple cleartext password that is sent as part of the OSPFv2 message. The receiving OSPFv2 router must be configured with the same cleartext password to accept the OSPFv2 message as a valid route update.
Configuration:
NX7k-01#
interface Ethernet1/2
no switchport
ip address 192.168.20.1/30
ip ospf authentication
ip ospf authentication-key learndut
ip router ospf 10 area 0.0.0.0
no shutdown
router ospf 10
router-id 1.1.1.1version 9.3(9) Bios:version
NX7k-02#
interface Ethernet1/2
no switchport
ip address 192.168.20.2/30
ip ospf authentication
ip ospf authentication-key learndut
ip router ospf 10 area 0.0.0.0
no shutdown
router ospf 10
router-id 2.2.2.2
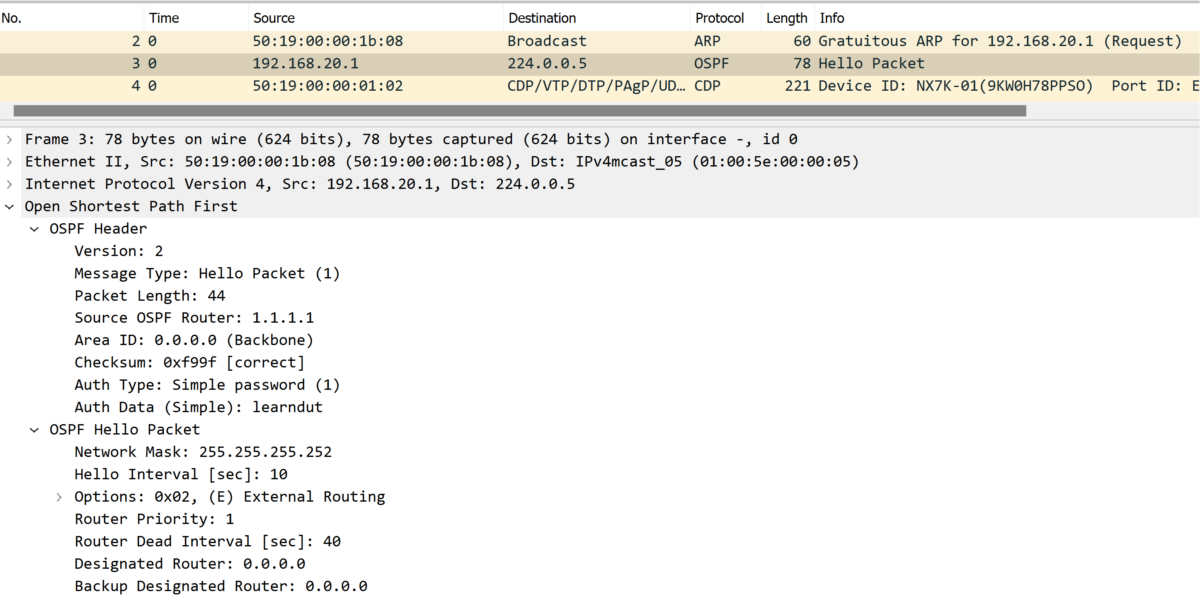
This option is not recommended from security perspective, because the password is in cleartext, anyone who can watch traffic on the network can learn the password.
This can easily illustrated from a Wireshark capture and you can see the password “learndut” in the OSPF header:
MD5 authentication digest
For more security, you should use MD5 authentication to authenticate OSPFv2 messages.
You configure a password that is shared at the local router and all remote OSPFv2 neighbors. For each OSPFv2 message, Cisco NX-OS creates an MD5 one-way message digest based on the message itself and the encrypted password:
1- The interface sends a digest with the OSPFv2 message (based on the OSPF message & the encrypted password)
2- The receiving OSPFv2 neighbor validates the digest using the same encrypted password: If the message has not changed, the digest calculation is identical and the OSPFv2 message is considered valid.
Configuration:
We need to create the key chain for this authentication configuration.
What is Key chain: A key chain is a list of keys. Each key consists of a key string, which is also called the password or passcode. A key-string is essential for a key to be operational. Each key is identified by a unique key ID. To authenticate the OSPFv2 packets, it is essential that the cryptographic authentication algorithm be configured with a key.
The authentication key on a key chain is valid for a specific time period called lifetime. An SA has the following configurable lifetimes:
- Accept lifetime
- Send lifetime
When key chain has more than one key, OSPF selects the key that has the maximum life time. Key having an infinite lifetime is preferred. If keys have the same lifetime, then key with the higher key ID is preferred.
NX7k-01#
key chain learnduty
key 1
key-string cisco
interface Ethernet1/2
no switchport
ip address 192.168.20.1/30
ip ospf authentication message-digest
ip ospf authentication key-chain learnduty
ip router ospf 10 area 0.0.0.0
no shutdown
router ospf 10
router-id 1.1.1.1
area 0.0.0.0 authentication message-digestNX7k-01#
key chain learnduty
key 1
key-string cisco
interface Ethernet1/2
no switchport
ip address 192.168.20.2/30
ip ospf authentication message-digest
ip ospf authentication key-chain learnduty
ip router ospf 10 area 0.0.0.0
no shutdown
router ospf 10
router-id 1.1.1.1
area 0.0.0.0 authentication message-digest
Checking again the Wireshark capture for this authentication method:
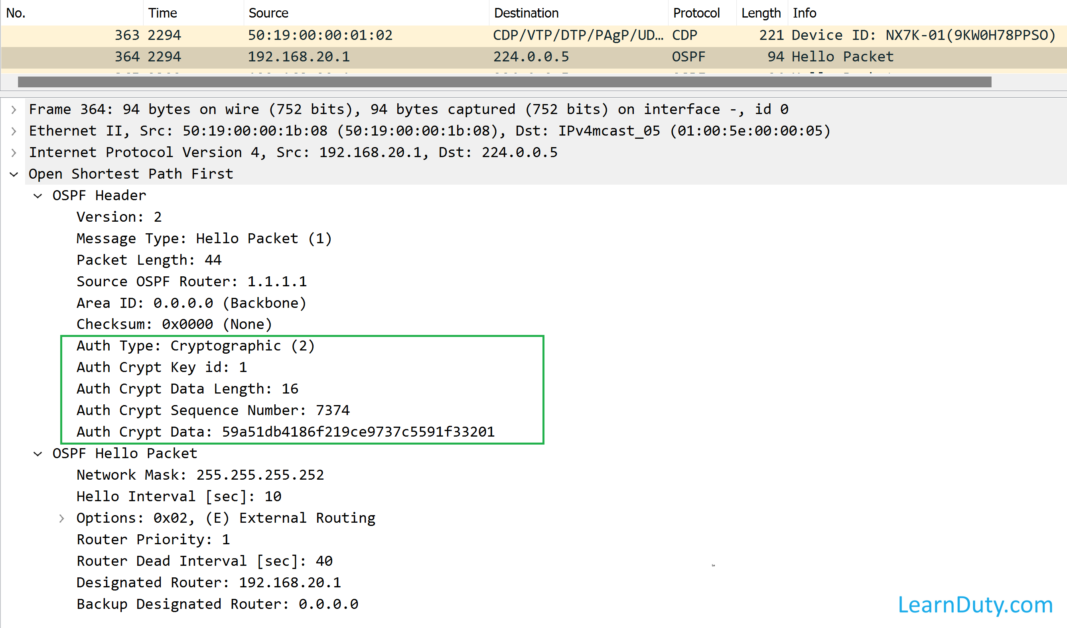
We can see that Auth Type is Cryptographic along with a key ID and a non-decreasing sequence number:
- MD5 authentication includes a sequence number with each OSPFv2 message to ensure that no message is replayed in the network (prevents replay attacks).
- This method uses the MD5 algorithm to compute a hash value from the contents of the OSPF packet and a password (or key).
- The receiver, which knows the same password, calculates its own hash value. If nothing in the message changes, the hash value of the receiver must match the hash value of the sender which is transmitted with the message.
Verification:
NX7K-02(config-if)# show ip ospf neighbors
OSPF Process ID 10 VRF default
Total number of neighbors: 1
Neighbor ID Pri State Up Time Address Interface
1.1.1.1 1 FULL/DR 00:00:36 192.168.20.1 Eth1/2
Reference: Cisco.com
