Private VLAN Forwarding Explained (With LAB and Packet Flows)
Contents
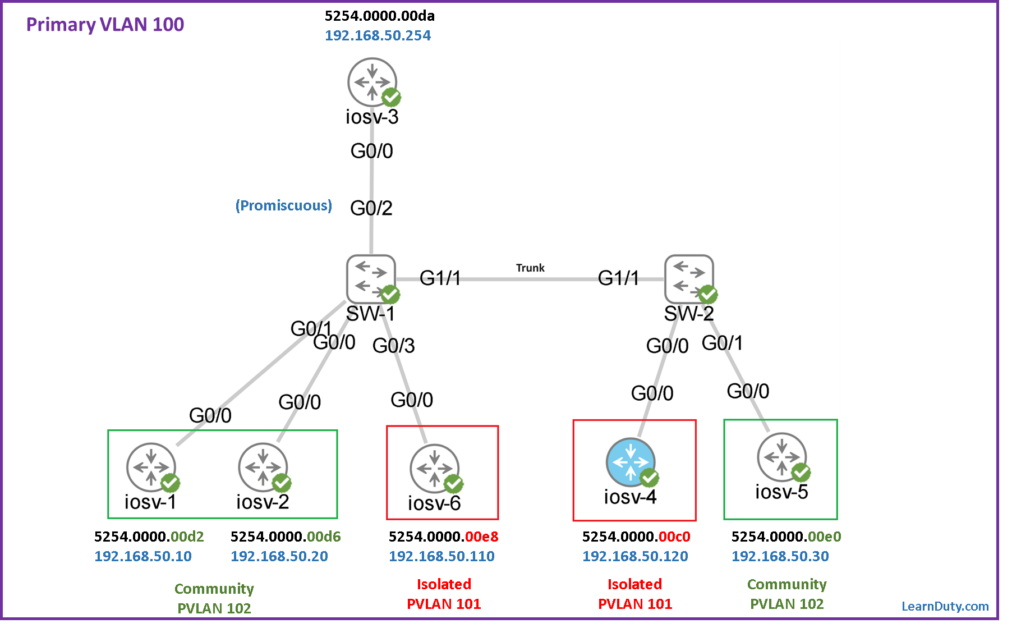
Topology
Configuration
SW-1:
SW1#sh run
version 15.2
hostname SW1
vtp mode transparent
!
vlan 100
private-vlan primary
private-vlan association 101-102
!
vlan 101
private-vlan isolated
!
vlan 102
private-vlan community
!
interface GigabitEthernet0/0
switchport private-vlan host-association 100 102
switchport mode private-vlan host
negotiation auto
!
interface GigabitEthernet0/1
switchport private-vlan host-association 100 102
switchport mode private-vlan host
negotiation auto
!
interface GigabitEthernet0/2
switchport private-vlan mapping 100 101-102
switchport mode private-vlan promiscuous
negotiation auto
!
interface GigabitEthernet0/3
switchport private-vlan host-association 100 101
switchport mode private-vlan host
negotiation auto
!
interface GigabitEthernet1/1
switchport trunk encapsulation dot1q
switchport mode trunk
negotiation autoSW-2:
SW-2#sh run
Building configuration...
version 15.2
!
hostname SW-2
!
vtp mode transparent
!
vlan 100
private-vlan primary
private-vlan association 101-102
!
vlan 101
private-vlan isolated
!
vlan 102
private-vlan community
interface GigabitEthernet0/0
switchport private-vlan host-association 100 101
switchport mode private-vlan host
negotiation auto
!
interface GigabitEthernet0/1
switchport private-vlan host-association 100 102
switchport mode private-vlan host
negotiation auto
!
interface GigabitEthernet1/1
switchport trunk encapsulation dot1q
switchport mode trunk
negotiation autoConfig Verification
SW-1:
SW1#show vlan private-vlan
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
100 101 isolated Gi0/2, Gi0/3
100 102 community Gi0/0, Gi0/1, Gi0/2
SW1#show mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 5254.0000.00e5 DYNAMIC Gi1/1
102 5254.0000.00d2 DYNAMIC Gi0/1
102 5254.0000.00d6 DYNAMIC Gi0/0
102 5254.0000.00da DYNAMIC pv Gi0/2
102 5254.0000.00e0 DYNAMIC Gi1/1
102 5254.0000.00e5 DYNAMIC pv Gi1/1
100 5254.0000.00d2 DYNAMIC pv Gi0/1
100 5254.0000.00d6 DYNAMIC pv Gi0/0
100 5254.0000.00da DYNAMIC Gi0/2
100 5254.0000.00e0 DYNAMIC pv Gi1/1
100 5254.0000.00e8 DYNAMIC pv Gi0/3
101 5254.0000.00da DYNAMIC pv Gi0/2
101 5254.0000.00e5 DYNAMIC pv Gi1/1
101 5254.0000.00e8 BLOCKED Gi0/3
Total Mac Addresses for this criterion: 14
SW1#show int gi0/0 switchport
Name: Gi0/0
Switchport: Enabled
Administrative Mode: private-vlan host
Operational Mode: private-vlan host
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: 100 (VLAN0100) 102 (VLAN0102)
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 102 (VLAN0102)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
SW1#show int gi0/1 switchport
Name: Gi0/1
Switchport: Enabled
Administrative Mode: private-vlan host
Operational Mode: private-vlan host
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: 100 (VLAN0100) 102 (VLAN0102)
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 102 (VLAN0102)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
SW1#show int gi0/3 switchport
Name: Gi0/3
Switchport: Enabled
Administrative Mode: private-vlan host
Operational Mode: private-vlan host
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: 100 (VLAN0100) 101 (VLAN0101)
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 101 (VLAN0101)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
SW1#show int gi0/2 switchport
Name: Gi0/2
Switchport: Enabled
Administrative Mode: private-vlan promiscuous
Operational Mode: private-vlan promiscuous
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: 100 (VLAN0100) 101 (VLAN0101) 102 (VLAN0102)
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 101 (VLAN0101) 102 (VLAN0102)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: noneCode language: PHP (php)
SW-2:
SW-2#show vlan private-vlan
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
100 101 isolated Gi0/0
100 102 community Gi0/1
SW-2#show mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 5254.0000.00cf DYNAMIC Gi1/1
100 5254.0000.00c0 DYNAMIC pv Gi0/0
100 5254.0000.00d2 DYNAMIC pv Gi1/1
100 5254.0000.00da DYNAMIC Gi1/1
100 5254.0000.00e0 DYNAMIC pv Gi0/1
101 5254.0000.00c0 BLOCKED Gi0/0
101 5254.0000.00da DYNAMIC pv Gi1/1
102 5254.0000.00d2 DYNAMIC Gi1/1
102 5254.0000.00da DYNAMIC pv Gi1/1
102 5254.0000.00e0 DYNAMIC Gi0/1
Total Mac Addresses for this criterion: 10
SW-2#show int gi0/0 switchport
Name: Gi0/0
Switchport: Enabled
Administrative Mode: private-vlan host
Operational Mode: private-vlan host
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: 100 (VLAN0100) 101 (VLAN0101)
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 101 (VLAN0101)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
SW-2#show int gi0/1 switchport
Name: Gi0/1
Switchport: Enabled
Administrative Mode: private-vlan host
Operational Mode: private-vlan host
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: 100 (VLAN0100) 102 (VLAN0102)
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 102 (VLAN0102)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
Code language: PHP (php)Connectivity Verification
we verified the basic connectivity between Hosts:
- Hosts in Community Private VLAN can reach each other and also can reach the Promiscuous port.
- Hosts in Isolated Private VLAN can only reach to Promiscuous port.
- Promiscuous can reach to all hosts
iosv-1#ping 192.168.50.20
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.50.20, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/3 ms
iosv-1#ping 192.168.50.30
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.50.30, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/5/6 ms
iosv-1#ping 192.168.50.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.50.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/3/4 ms
iosv-1#ping 192.168.50.110
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.50.110, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
iosv-1#ping 192.168.50.120
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.50.120, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Code language: PHP (php)How Private VLAN Forwarding works
We will see how traffic forwarding is enforced with Private VLAN by analyzing the MAC address table of the switch:
SW1#show mac address-table
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 5254.0000.00e5 DYNAMIC Gi1/1
102 5254.0000.00d2 DYNAMIC Gi0/1
102 5254.0000.00d6 DYNAMIC Gi0/0
102 5254.0000.00da DYNAMIC pv Gi0/2
102 5254.0000.00e0 DYNAMIC Gi1/1
102 5254.0000.00e5 DYNAMIC pv Gi1/1
100 5254.0000.00d2 DYNAMIC pv Gi0/1
100 5254.0000.00d6 DYNAMIC pv Gi0/0
100 5254.0000.00da DYNAMIC Gi0/2
100 5254.0000.00e0 DYNAMIC pv Gi1/1
100 5254.0000.00e8 DYNAMIC pv Gi0/3
101 5254.0000.00da DYNAMIC pv Gi0/2
101 5254.0000.00e5 DYNAMIC pv Gi1/1
101 5254.0000.00e8 BLOCKED Gi0/3
Code language: PHP (php)
Traffic from Hosts in Community VLAN (carried in Secondary VLAN):
First, let’s focus on the communication for the Hosts in the Community Private VLAN 102:
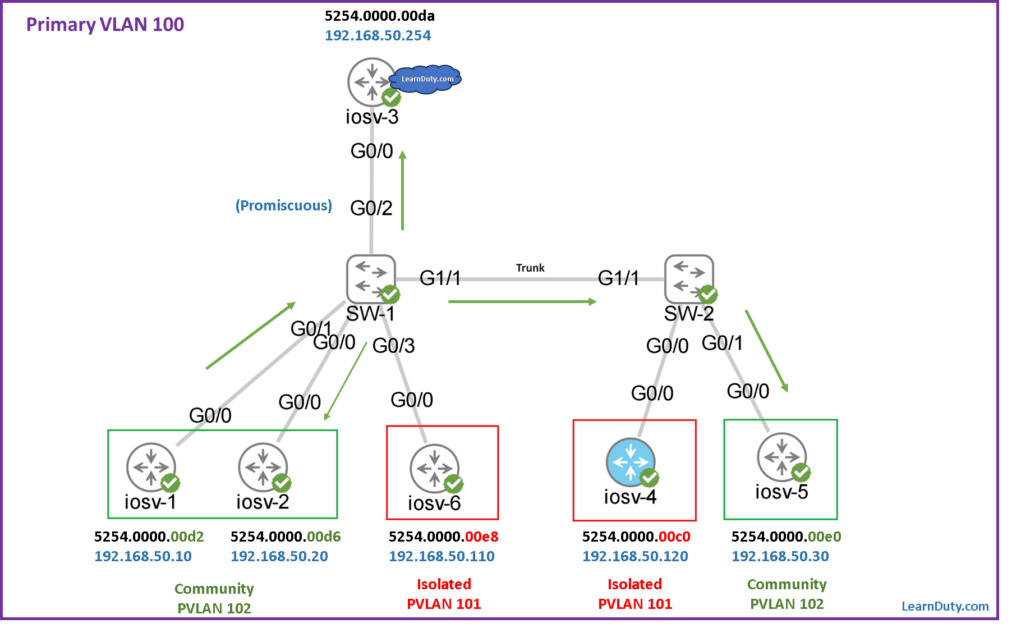
From iosv-1 to iosv-2 (5254.0000.00d6):
For example, the traffic stream from the host iosv-1 toward the promiscuous port is carried in the secondary VLAN 102 (community):
So traffic from host iosv-1 hit the switch SW-1 and it’s carried in community Secondary VLAN 102:
✅ For this flow, the destination is iosv-2 (with MAC 5254.0000.00d6) which is also in the same community VLAN 102, it will be forwarded in VLAN 102 via interface Gi0/0, as per the MAC table entry below:
SW1#
Vlan Mac Address Type Ports
---- ----------- -------- -----
102 5254.0000.00d6 DYNAMIC Gi0/0Code language: PHP (php)From iosv-1 to Promiscuous port (5254.0000.00da):
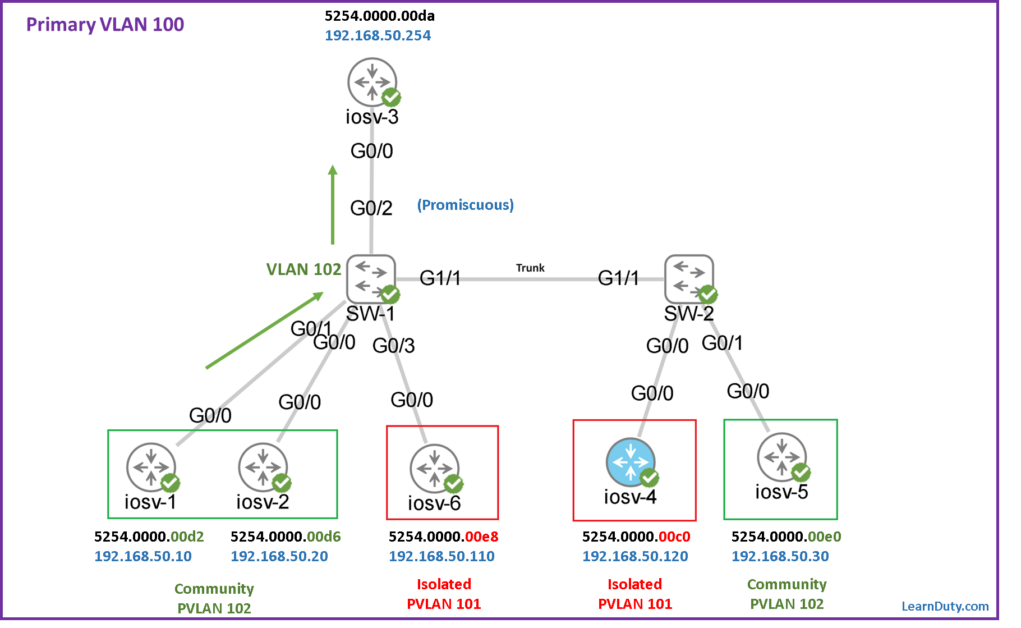
✅ Traffic sourced from the hosts (in secondary VLANs) to destination Promiscuous port (MAC 5254.0000.00da) is carried in Secondary VLAN.
Example, traffic sourced from host iosv-1 to Promiscuous port is carried in secondary VLAN 102 and it will use the entry below in the MAC table of secondary VLAN 102:
SW1#
Vlan Mac Address Type Ports
---- ----------- -------- -----
102 5254.0000.00da DYNAMIC pv Gi0/2Code language: PHP (php)The “DYNAMIC pv” type in the previous MAC entry is an indication that this MAC was originally learned from the Primary VLAN (traffic coming from Promiscuous port) and replicated in the Secondary VLAN MAC table as “DYNAMIC pv”.
Traffic from Promiscuous toward hosts in Secondary VLANs (carried in Primary VLAN):
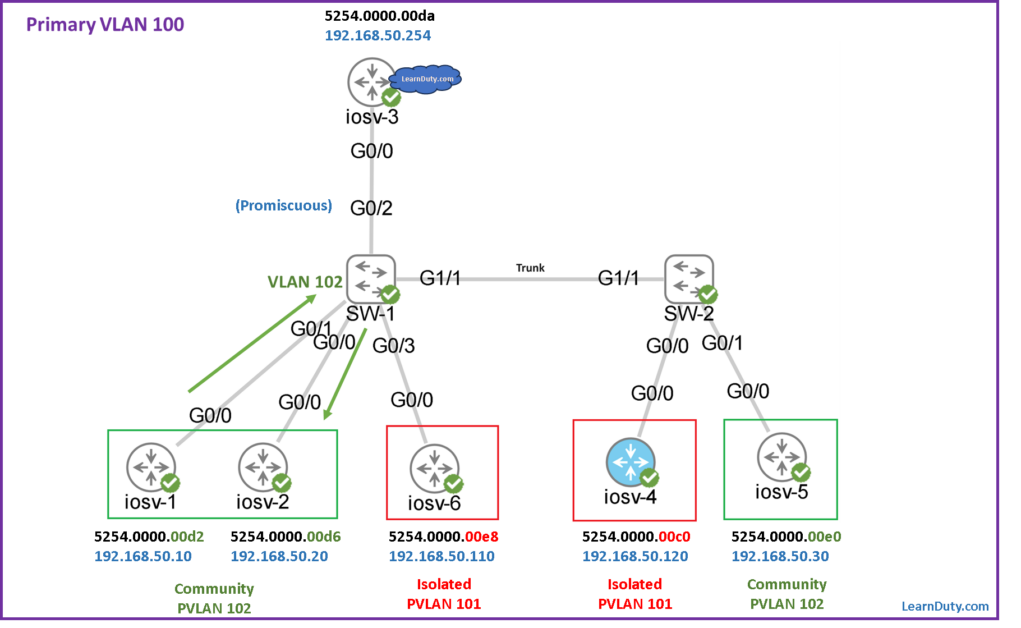
Example-1: From Promiscuous port to iosv-1 (5254.0000.00d2):
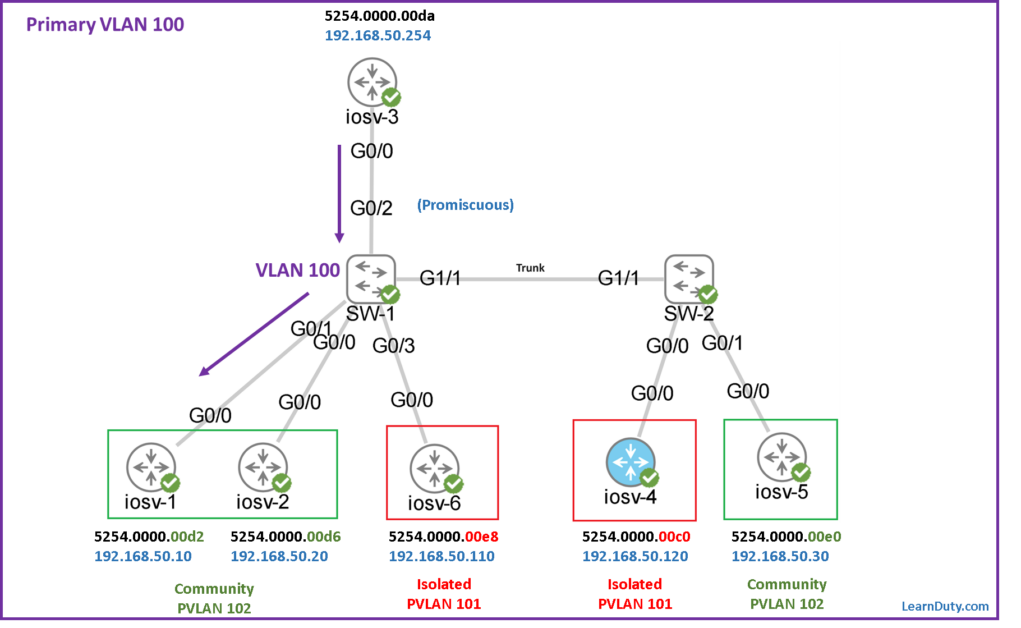
✅ For the traffic from the Promiscuous port to the hosts in secondary VLANs, it will be carried in the Primary VLAN 100:
- For example, if destination is iosv-1, it will use the entry with MAC “5254.0000.00d2” below.
- Note that we see type as “DYNAMIC pv” because this entry was originally learned in the secondary community VLAN 102 and replicated to the Primary VLAN 100 as you can see below:
SW1#
Vlan Mac Address Type Ports
---- ----------- -------- -----
100 5254.0000.00d2 DYNAMIC pv Gi0/1Code language: PHP (php)Example-2: From Promiscuous port to iosv-5 (5254.0000.00e0):
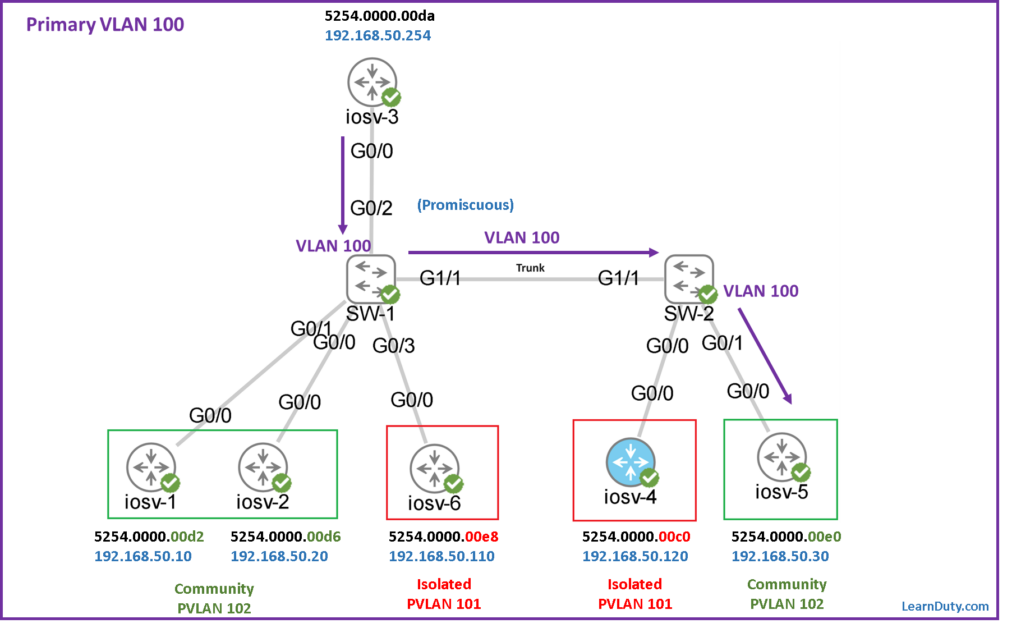
From Promiscuous port to destination iosv-5, it will use the entry with MAC “5254.0000.00e0” below in SW-1:
SW1# show mac address-table
Vlan Mac Address Type Ports
---- ----------- -------- -----
100 5254.0000.00e0 DYNAMIC pv Gi1/1Code language: PHP (php)
Then, it will carried and trunked in Primary VLAN 100 and reaches SW-2, where it will leverage the following MAC entry below for destination iosv-5(MAC “5254.0000.00e0“):
SW-2#show mac address-table
Vlan Mac Address Type Ports
---- ----------- -------- -----
100 5254.0000.00e0 DYNAMIC pv Gi0/1Code language: PHP (php)Basically, the following entries in Primary VLAN 100 MAC table indicates that the traffic from the Promiscuous port which is carried in the Primary VLAN is allowed to reach all hosts in corresponding secondary VLANs (in either Isolated and Community VLANs), and that’s the expected behavior.
SW1#
Vlan Mac Address Type Ports
---- ----------- -------- -----
100 5254.0000.00d2 DYNAMIC pv Gi0/1
100 5254.0000.00d6 DYNAMIC pv Gi0/0
100 5254.0000.00da DYNAMIC Gi0/2
100 5254.0000.00e0 DYNAMIC pv Gi1/1
100 5254.0000.00e8 DYNAMIC pv Gi0/3Code language: PHP (php)Traffic between hosts in Isolated VLAN:
Example: traffic from iosv-6 to iosv-4:
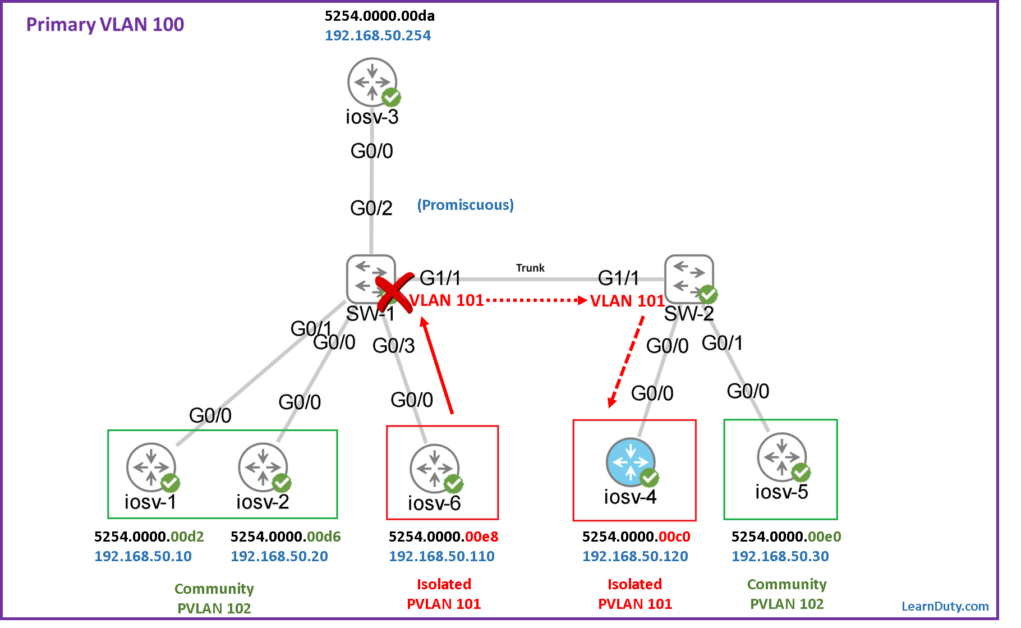
For the traffic from host iosv-6 to iosv-4, traffic hit SW-1 is carried in the secondary isolated VLAN 101.
❌ According the MAC table of isolated VLAN 101 (in SW-1), if traffic which came from host iosv-6 in VLAN 101 and destination is iosv-4 (MAC 5254.0000.00c0), traffic is Blocked:
SW1#
101 5254.0000.00c0 BLOCKED Gi1/1
101 5254.0000.00e8 BLOCKED Gi0/3
101 5254.0000.00da DYNAMIC pv Gi0/2Code language: PHP (php)“BLOCKED” indicates traffic toward this MAC is blocked, as a result iosv-6 can’t reach iosv-4 (this is how the enforcement to deny traffic between hosts in isolated VLAN is achieved).
✅ But, the traffic coming from hosts in secondary isolate VLAN 101 toward toward the Promiscuous port (MAC 5254.0000.00da) is permitted (as per the third entry below):
We see “DYNAMIC pv” because this MAC was originally learned in the Primary VLAN 100 and replicated in secondary Isolated VLAN MAC table to allow traffic from isolated VLAN hosts to reach the Promiscuous port.
Traffic between Community VLAN hosts to an Isolated VLAN Hosts:
Now, let’s look on how the traffic between Community VLAN hosts to an Isolated Hosts is denied:
❌ The interesting part here that there is no MAC entry for destination with type “BLOCKED” flag to enforce the block of traffic between community and Isolated VLAN:
Instead, there is no entry at all in MAC table for destination in different secondary VLAN.
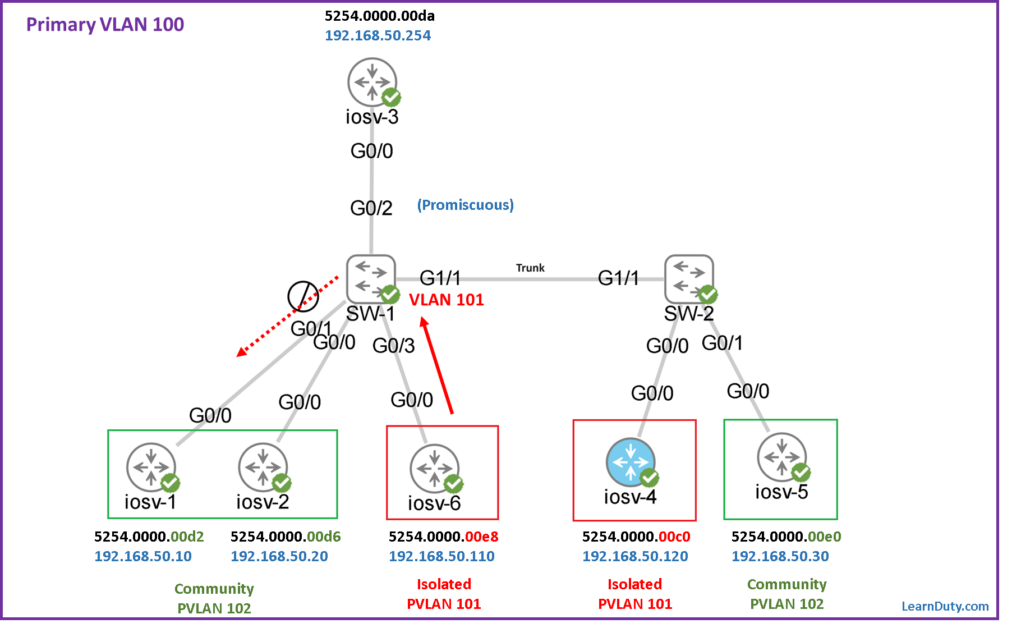
For example, if iosv-6 (part of isolated VLAN 101) wants to communicate with iosv-1 (part of community VLAN 102):
Traffic will hit the SW-1 and be carried in Isolated VLAN 101, but the destination iosv-1 (WITH MAC 5254.0000.00d2) doesn’t even exist in MAC table of VLAN 101. As a result, hosts in different secondary VLANs can’t talk to each other.
SW1#show mac address-table vlan 101
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
101 5254.0000.00c0 BLOCKED Gi1/1
101 5254.0000.00da DYNAMIC pv Gi0/2
101 5254.0000.00e5 DYNAMIC pv Gi1/1
101 5254.0000.00e8 BLOCKED Gi0/3Code language: PHP (php)Same for opposite, from community to isolated secondary VLAN.

![Explore The BGP Path Selection Attributes [Explained with Labs]](https://learnduty.com/wp-content/uploads/2022/07/image-28-800x450.png)