Microsoft Hyper-V – Networking concepts Basics

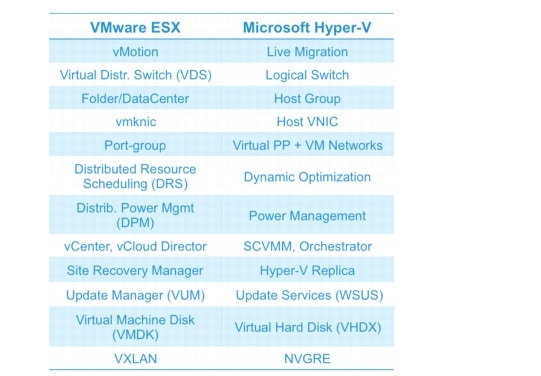
Before we start, lets take a look at VMware ESXi vs Microsoft Hyper V Terminology:
Contents
The Hyper-V virtual switch
The Hyper-V virtual switch is really a relabeling of a network adapter. That network adapter cannot have two identities. So, once it is assigned to a virtual switch, it has no other purpose and cannot be accessed in any other way. The Hyper-V virtual switch occupies the network adapter entirely.
Once you assign a network adapter to a virtual switch identity, the operating system ceases to recognize that NIC as a network adapter. That means you won’t see it listed as an adapter in the Network Connections folder in Windows Settings. So, the procedures that you are used to using through the operating system to manage and adjust adapters can’t be used for your virtual switch.
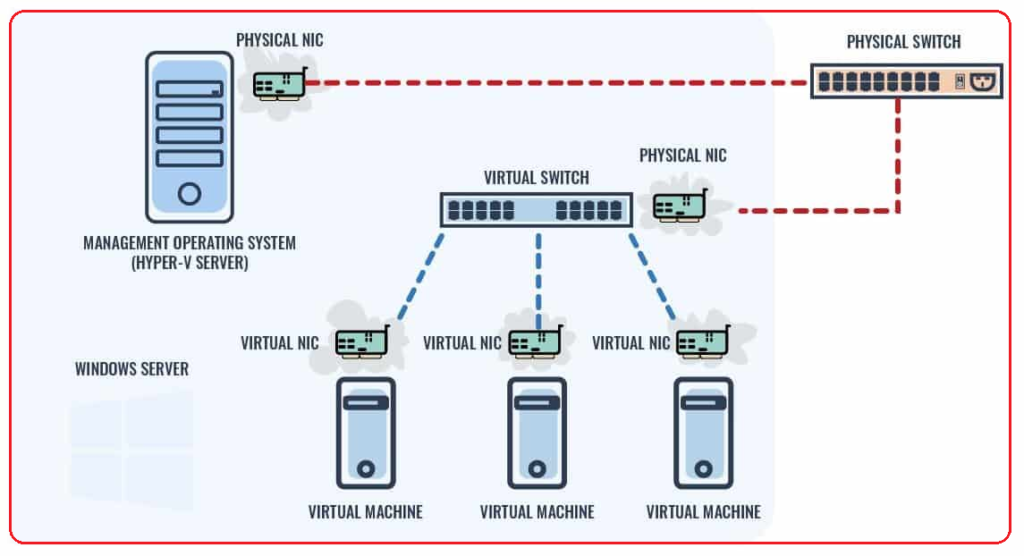
Here are some facts about virtual switches to keep in mind:
- Each VM connects to a virtual switch via a virtual NIC.
- Many virtual NICs can connect to one virtual switch.
- VM-to-VM communication has to pass through the virtual switch.
- In this basic configuration, VM-to-server communication has to pass through a virtual switch and a physical switch.
Three Types of Virtual Switches:
Virtual machines have numerous virtualized resources. One type is the virtual network adapter. One or more virtual network adapters are added to a virtual machine, and then each virtual adapter is attached to a virtual switch that was created at the Hyper-V host level. A Hyper-V host can have many virtual switches created. Three types of virtual switches are available: external, internal, and private, as shown in Figure below:
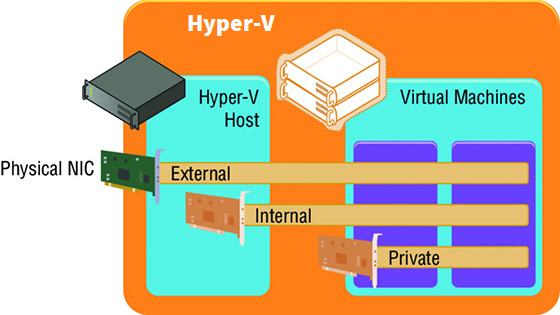
EXTERNAL VIRTUAL NETWORKS
External virtual networks are bound to a physical network card in the host. Virtual machines have access to this physical network via the physical NIC, which is linked to the external switch to which the virtual network adapter is connected. Virtual machines on the same virtual switch can also communicate with each other. If they are on different switches that can communicate through the physical network (that is, through routing), then they can also communicate. Each virtual machine sees a virtual network device, and the Hyper-V host still sees the network adapter; however, it will no longer use it. The network device on the Hyper-V host is the physical NIC, which is bound only to the Hyper-V extensible virtual switch, which means that it is being used by a Hyper-V virtual switch.
INTERNAL VIRTUAL NETWORKS
Internal virtual networks are not bound to a physical NIC and so, they cannot access any machine outside the physical server. An internal network is visible to the Hyper-V host and the virtual machines, which means that it can be used for communication between virtual machines and between virtual machines and the Hyper-V host. This can be useful if you are hosting services on the management partition, such as an iSCSI target, that you wish the virtual machines to be able to use. On both the Hyper-V host and virtual machines, a network device is visible that represents the internal virtual network.
PRIVATE VIRTUAL NETWORKS
Private virtual networks are visible only on virtual machines, and they are used for virtual machines to communicate with each other. This type of network could be used for virtual machines that are part of a guest cluster. The private network could be used for the cluster network, provided that all hosts in the cluster are running on the same Hyper-V host.
Creating a Virtual Switch
When the Hyper-V role is enabled on a server, you are given an option to create an external switch by selecting a network adapter on the host. If you choose this option, a virtual switch will already be present on the host and will be automatically configured to allow the management operating system to share the adapter so that an extra Hyper-V virtual Ethernet adapter will be present on the Hyper-V host. In general, I prefer not to create the virtual switches during Hyper-V role installation but to configure them post-installation. Also, as you will read later, if your deployment is a production deployment and you’re using System Center, then Virtual Machine Manager can do all of the switch configuration for you. I will, however, walk you through manually configuring virtual switches:
- Launch Hyper-V Manager.
- Select the Virtual Switch Manager action from the actions pane.
- In the navigation pane, select New Virtual Network Switch, and in the details pane, select the type of virtual switch to create. In this case, select External and click the Create Virtual Switch button.
- Replace the default New Virtual Switch name with a meaningful name that matches the naming standard for the switches that you have selected, such as, for example, External Switch. Optionally, you can enter notes.
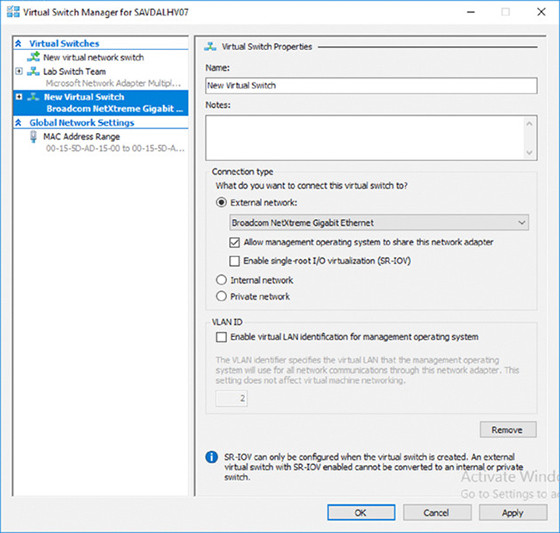
- If the switch type is external, you must select the specific network adapter or the NIC team that will be bound to the virtual switch from the list of available network adapters on the system, as shown in Figure 3.2. Note that you can change the type of switch on this screen by selecting another type of network, such as internal or private. Also note that network adapters/teams bound to other switches are still listed, but the creation will fail if they are selected.
VLANs in Hyper-V:
The use of VLANs is a major way that Hyper-V is different from VMWare ESXi. This is why you should clear your mind of everything you know about VMWare before implementing a Hyper-V project. The Hyper-V virtual switch automatically supports untagged frames and VLANs 1-4096 – this does not happen in ESXi. Also, Hyper-V does not have a “default” VLAN designation, so don’t worry about that.
In Hyper-V, you set up VLANs on the virtual adapters, not on the virtual switch.
If there are no VLANs on the physical network, you don’t need them on your Hyper-V hosts. If you use VLANs to separate out Layer 3 traffic, you should design your Hyper-V hosts to match.
The only VLAN configuration performed in the Hyper-V environment is within the properties of the virtual network adapter, as shown in Figure 3.9, where I set the VLAN ID for this specific network adapter for the virtual machine.
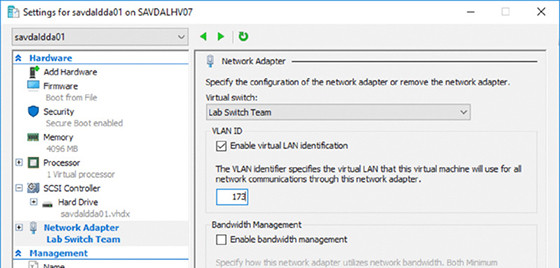
something might seem confusing: the option to configure a VLAN ID on the virtual switch itself. Does this setting then apply to every virtual machine connected to that virtual switch? No. As the explanation text in the dialog box explains, the VLAN ID configured on the virtual switch is applied to any virtual network adapters created in the management OS for the virtual switch, which allows the management OS to continue using a physical network adapter that has been assigned to a virtual switch. The VLAN ID configured on the switch has no effect on the virtual machine VLAN configuration.
SCVMM Networking Architecture
The first architectural component for SCVMM is the logical network, which helps model your physical network infrastructure and connectivity in SCVMM. Consider your virtualization environment and the networks to which the hosts and the virtual machines will need to connect.
The information can be summarized as follows:
- Create logical networks to mirror the physical networks that exist.
- Create logical networks to define the networks that have specific purposes.
- Identify logical networks that need to be isolated and identify the isolation method.
- Determine required network sites, VLANs, PVLANs, and IP pools required for each logical network and deploy them.
- Associate logical networks to host computers.
LOGICAL SWITCH
Earlier in this chapter, we created a virtual switch. Although it is possible to perform a manual configuration on a server-by-server basis, this can lead to inconsistencies and inhibits the automatic deployment of new Hyper-V hosts.
SCVMM has the logical switch component, which acts as the container for all virtual switch settings and ensures a consistent deployment across all servers using the logical switch. The automatic configuration using the logical switch is not only useful at deployment, but SCVMM will continue to track the configuration of the host compared to the logical switch, and if the configuration deviates from that of the logical switch, this deviation will be flagged as non-compliant, and that can then be resolved. This may be important in terms of ensuring compliance enforcement in an environment. If the logical switch is updated (for example, a new extension is added), all the Hyper-V hosts using it will automatically be updated.
If you had an existing Hyper-V server with virtual switches defined that will be standard switches in SCVMM, there was no way to convert them to logical switches prior to SCVMM 2016. A new option in SCVMM 2016, however, allows a standard switch to be converted to a logical switch. This conversion is facilitated through the properties of the host in the Fabric workspace: Select the Virtual Switches tab, select the standard switch, and then, at the bottom of the details, there is a button to convert to a logical switch. Click the button, select a logical switch that is equivalent to the connectivity, and the switch will be converted to a logical switch on the host.
It is also still possible to delete the standard switches and then re-create the switches as logical switches via SCVMM. To delete the standard switches, you would need to evacuate the host of virtual machines, which typically means that you have a cluster. However, with Windows Server 2012 and above, you can also move virtual machines with no downtime by using Shared Nothing Live Migration between any Hyper-V hosts, provided that they have a 1Gbps network connection. Of course, none of this should be required if you ensure that all configuration is done through SCVMM initially after planning out the logical networks, logical switches, and all other components before deploying Hyper-V hosts.
VM NETWORKS
While the logical network provides the modeling of the networks available in the environment and the desired isolation, the goal for virtualization is to separate and abstract these logical networks from the actual virtual machines. This abstraction is achieved through the use of VM networks, which is another networking architectural component in SCVMM. Through the use of VM networks, the virtual machines have no idea of the underlying technology used by the logical networks.
For example, whether VLANs are used on the network fabric. Virtual machine virtual network adapters can be connected to only a VM network. When Network Virtualization is used, the customer address (CA) space is defined as part of the VM network, allowing specific VM subnets to be created as needed within the VM network.
References:
http://devguis.com/hyper-v-windows-server-2016-chapter-3-virtual-networking.html
Hyper-V Networking Guide


![OSPF DR and BDR Election Explained [with Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-33.png?v=1647900046)
![OSPF Neighbor Adjacency Requirements [With Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-23-418x450.png?v=1647900064)
![OSPF Neighbor States Explained [Step by Step]](https://learnduty.com/wp-content/uploads/2022/03/image-13.png?v=1647900076)
![OSPF Area Types Explained and Configuration [Demystified]](https://learnduty.com/wp-content/uploads/2022/03/image-8.png?v=1647900083)