TACACS Configuration in ACI 4.2 – ISE Integration
Contents
I- Configure TACACS Provider
Navigate to: Admin > AAA > Authentication > TACACS > Create TACACS+ Provider
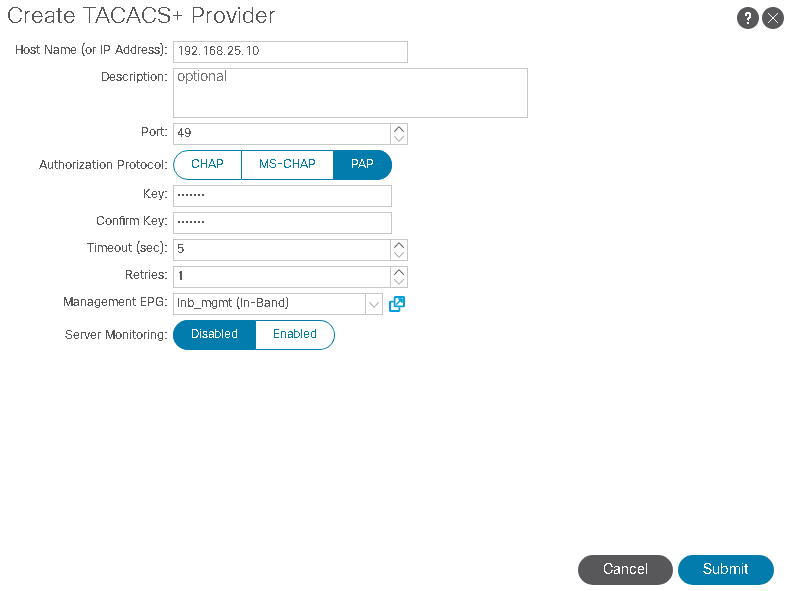
- Enter The TACACS+ host name or IP address:
Note: If the APIC is configured for in-band management connectivity, choosing an out-of-band management endpoint group for TACACS+ access does not take effect. [Cisco ACI Help]
- Tacacs+ port: The TCP port number to be used when making connections to the TACACS+ daemon. The range is from 1 to 65535. The default is 49.
- The Authorization Protocol must match on TACACS Server side.
- Key: This needs to match the configuration on the TACACS server which we will go over later in the ACS and ISE configuration
- Timeout: The amount of time allowed for a login attempt to occur before giving up (measured in seconds)
- Retries: The number of automatic re-try login attempts allowed for a single authentication submission
- Management EPG: The management EPG used to connect to the TACACS server. Chose the management EPG, Inband or OOB management EPG (inband in our case).
- Server Monitoring: Used to determine if the TACACS server is alive. This option uses the TACACS protocol login to check if the TACACS server is alive.
Note: For ACI versions prior to v4: Create the TACACS+ provider group.
II- Create the Login Domain for TACACS+.
The next step is to create the Login Domain and associate it to the newly created TACACS Provider.
To create a Login Domain navigate to the following APIC web GUI path:
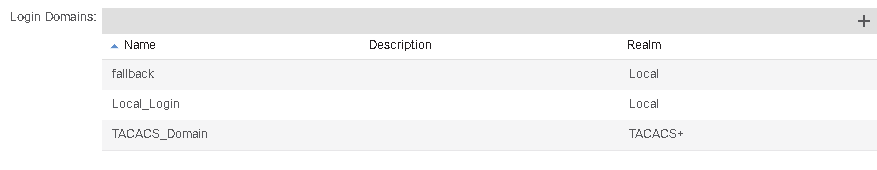
Admin -> AAA -> AAA Authentication -> Login Domains
In the Navigation pane, choose AAA Authentication > Login Domains.
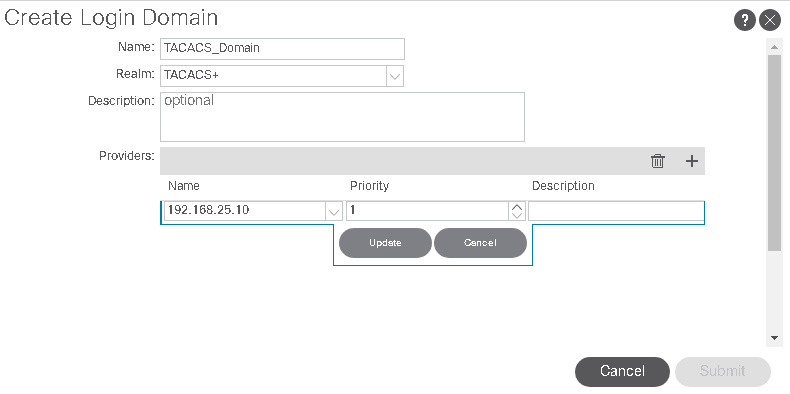
This Login Domain appears in the Domain drop-down list in the APIC GUI login screen:
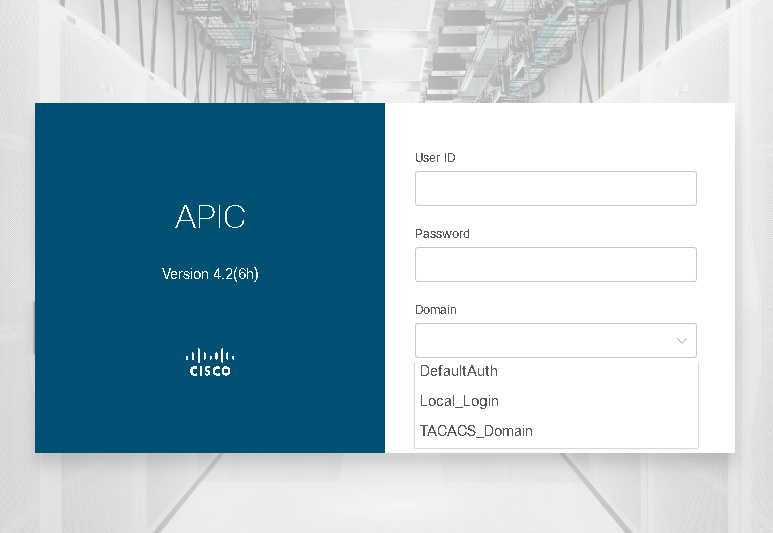
Note: Following good practice guidelines, create an additional Login Domain that has a Realm of Local. This local Login Domain will allow users to use local APIC credentials as fall-back access when the TACACS+ server is unavailable:
III- Set the DefaultAuth login:
If a Login Domain is not selected, the built-in DefaultAuth login domain is used. To make the APIC default to the TACACS+ login domain, change the default Login Domain behavior by navigating to the following APIC web GUI path: Admin -> AAA -> AAA Authentication
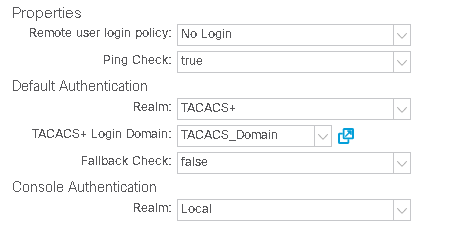
Note: Make sure to leave/set the Fallback Check property to false. Setting the Fallback Check property to true may cause local logins to fail.
* Fall Back use case, Local Domain
If you did not create an additional Login Domain for local authentication, and you forgot your TACACS credentials, ACI includes a fallback Login Domain. The fallback Login Domain cannot be deleted and is set to use local authentication by default. In order to login to the fallback Login Domain you must use this syntax:
APIC GUI: apic:LOGIN_DOMAIN_HERE\\LOCAL_USERNAME_HERE
APIC CLI: apic#LOGIN_DOMAIN_HERE\\LOCAL_USERNAME_HERE
To login to the local admin account you would use the following APIC GUI and CLI syntaxes:
APIC GUI: apic:fallback\\admin
APIC CLI: apic#fallback\\admin
ISE TACACS Profile:
In ISE, Create TACACS Profiles with the following attributes:
Read-Write-All profile which will allow read and write access to all of ACI. The custom attribute we need to assign has two important values, Attribute: cisco-av-pair and Attribute Value. The Attribute Value, known as the AVPair, is what actually determines user permissions. AVPairs have the below syntax:
Write Privileges: shell:domains=ACI_SECURITY_DOMAIN_HERE/ACI_USER_ROLE_HERE/
Read Privileges: shell:domains=ACI_SECURITY_DOMAIN_HERE//ACI_USER_ROLE_HERE
Example:
For our Read-Write-All shell profile, we want to assign admin privileges to all objects. To do this we will use the following AVPair:
shell:domains=all/admin/
all refer to all ACI Security Domain, and admin refers to the admin role in ACI.
If multiple roles are required, separate them with a pipe (|) character. The UID can only be provided after read privileges are assigned. For example:
shell:domains=all/aaa|admin/aaa|admin(16001)
– domain: all
– write privilege: aaa and admin
– read privilege: aaa and admin

![OSPF DR and BDR Election Explained [with Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-33.png?v=1647900046)
![OSPF Neighbor Adjacency Requirements [With Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-23-418x450.png?v=1647900064)
![BGP Route Reflector [Explained & Configuration]](https://learnduty.com/wp-content/uploads/2022/02/image-79-531x450.png?v=1647900109)
![Cisco Catalyst 9000 Switches Upgrade [Step by step]](https://learnduty.com/wp-content/uploads/2022/02/image-54.png?v=1647900155)
![L2 Interface Policy – Per Port VLAN in Cisco ACI [Explained]](https://learnduty.com/wp-content/uploads/2022/02/image-42.png?v=1647900173)