ERSPAN Configuration Example (Encapsulated Remote SPAN) [EVE-ng]
![ERSPAN Configuration Example (Encapsulated Remote SPAN) [EVE-ng]](https://learnduty.com/wp-content/uploads/2023/02/image-2.png)
Contents
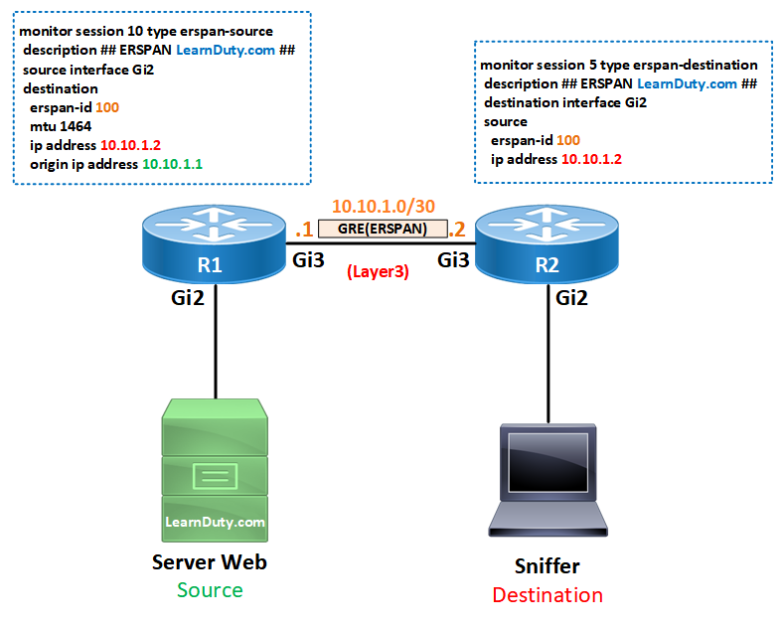
ERSPAN Topology
Below is the topology for ERSPAN configuration:
- The source traffic that we want to capture is from the server web (learnduty.com) connected to R1
- The destination or sniffer (Wireshark) is on R2 side connected to the interface Gi2
let’s dive into the ERSPAN configuration
ERSPAN Configuration
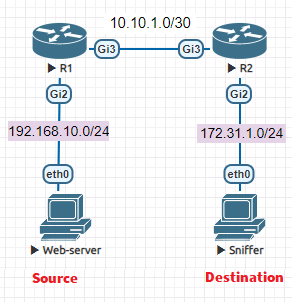
R1 Configuration
On R1, we will configure the source for the ERSPAN:
- We specify the type of the ERSPAN as erspan-source
- configure The origin (source) and the destination of the GRE ERSPAN tunnel.
interface GigabitEthernet2
ip address 192.168.10.254 255.255.255.0
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 10.10.1.1 255.255.255.252
negotiation auto
no mop enabled
no mop sysid
!
monitor session 10 type erspan-source
description ## ERSPAN LearnDuty.com ##
source interface Gi2
destination
erspan-id 100
mtu 1464
ip address 10.10.1.2
origin ip address 10.10.1.1
R2 Configuration
Also, on the destination (where the sniffer resides), we configure ERSPAN type as erspan-destination:
- Destination is the interface to the sniffer
- source is the IP of the interface which received the ERSPAN GRE traffic (GRE ERSPAN tunnel destination)
Make sure that the ERSPAN ID is the same of the source and destination device.
interface GigabitEthernet2
ip address 172.31.1.254 255.255.255.0
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 10.10.1.2 255.255.255.252
negotiation auto
no mop enabled
no mop sysid
!
monitor session 5 type erspan-destination
destination interface Gi2
source
erspan-id 100
ip address 10.10.1.2
Note: In our case, the ERSPAN session is starting and terminating at the switch level, but, it’s possible to extend it at the Sniffer level in case, the sniffer support ERSPAN (to perform decapsulation of the traffic)
ERSPAN Verification
On R1:
R1#show monitor session all
Session 10
----------
Type : ERSPAN Source Session
Status : Admin Enabled
Description : ## ERSPAN LearnDuty.com ##
Source Ports :
Both : Gi2
Destination IP Address : 10.10.1.2
MTU : 1464
Destination ERSPAN ID : 100
Origin IP Address : 10.10.1.1
On R2:
R2#show monitor session all
Session 5
---------
Type : ERSPAN Destination Session
Status : Admin Enabled
Destination Ports : Gi2
Source IP Address : 10.10.1.2
Source ERSPAN ID : 100
ERSPAN Wireshark capture
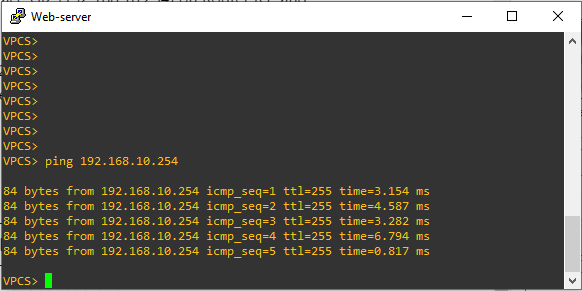
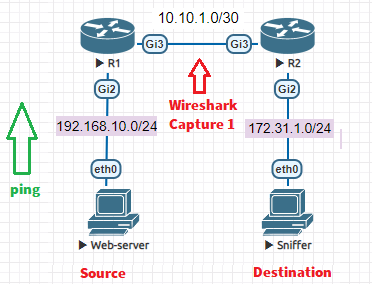
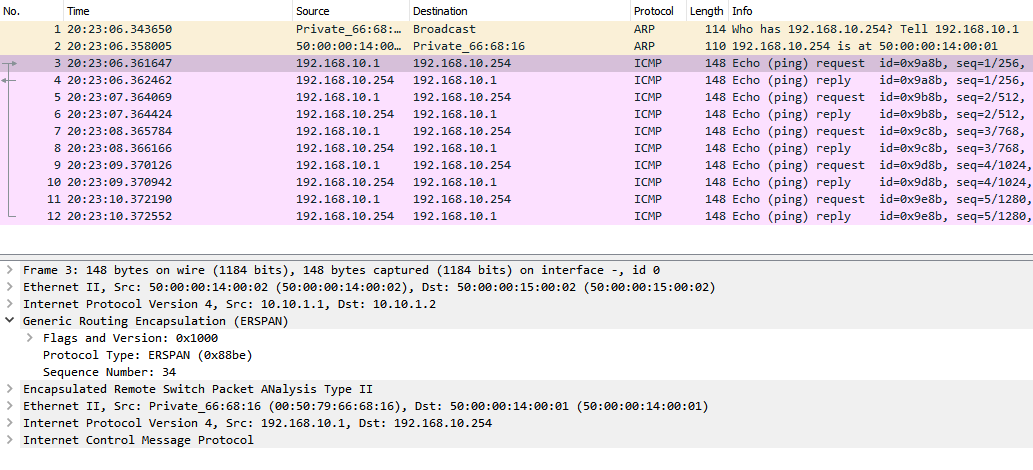
We will start a ping from Web-server (192.168.10.1) to interface Gi2 (192.168.10.254) on Router R1, and we will check 2 Wireshark capture:
- Wireshark Capture 1: on layer 3 link between R1 and R2 (GRE ERSPAN).
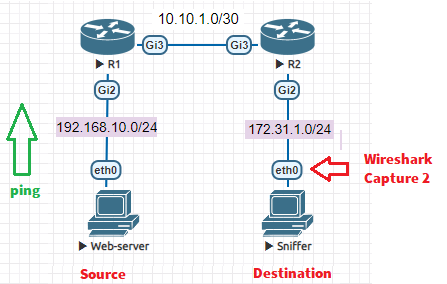
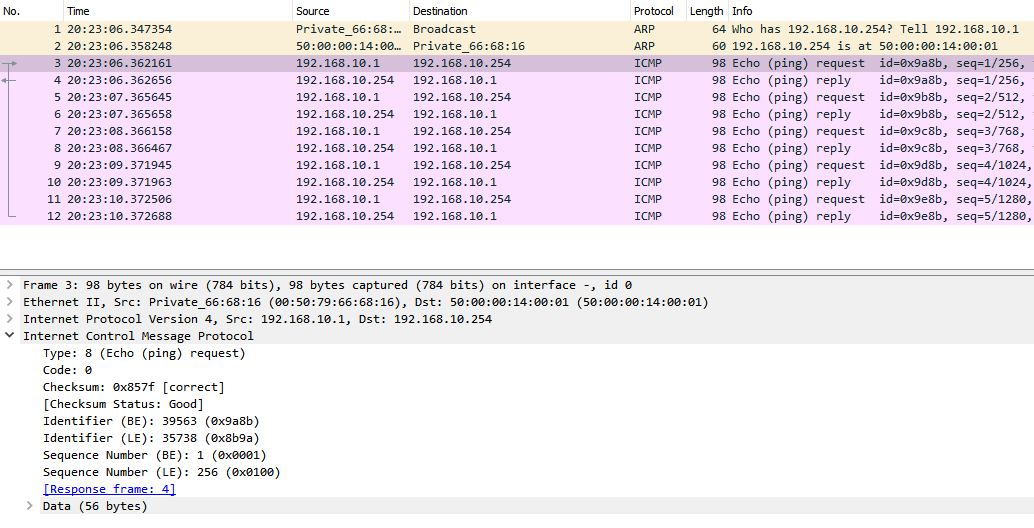
- Wireshark Capture 2: on the interface eth0 on the sniffer side to confirm that ERSPAN is working properly.
Wireshark Capture 1 (interface Gi3 R1 or R2):
Wireshark Capture 2 (interface Eth0 on the Sniffer):

![Explore The BGP Path Selection Attributes [Explained with Labs]](https://learnduty.com/wp-content/uploads/2022/07/image-28-800x450.png)