Cisco ACI RBAC (Role-Based Access Control) Overview
RBAC in Cisco ACI
The APIC provides access according to a user’s role through role-based access control (RBAC). An Cisco Application Centric Infrastructure (ACI) fabric user is associated with the following:
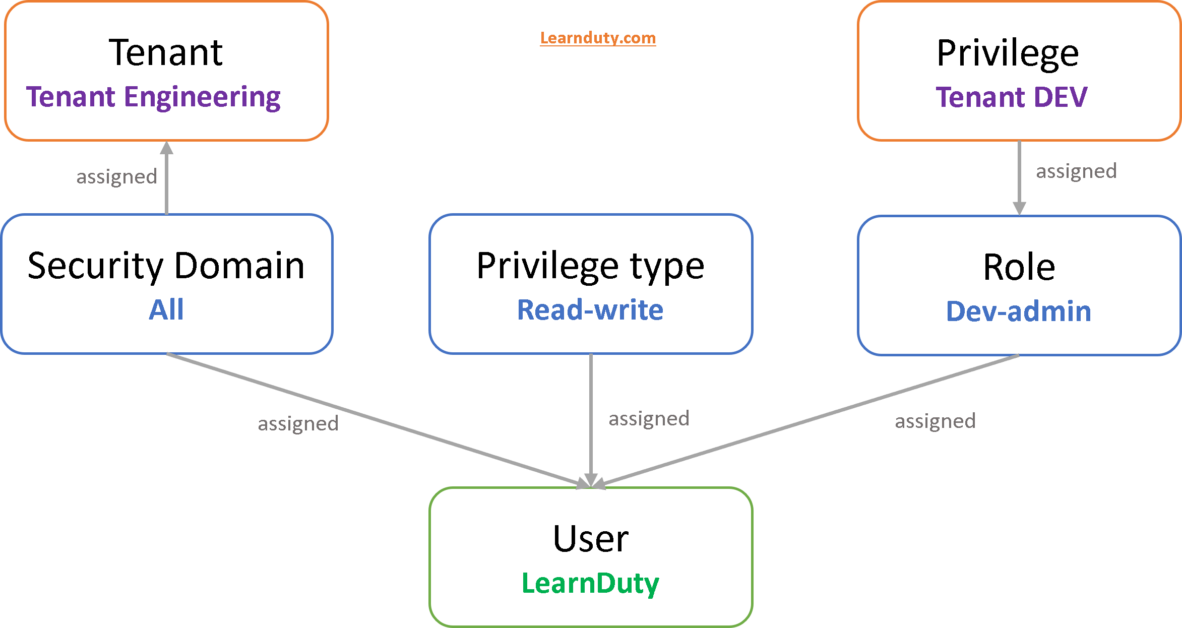
- Role (predefined or custom): which is a set of one or more privileges assigned to a user
Some roles contain other roles. The ‘admin’ role contains all privileges. - Privilege (one or multiples): which determine the managed objects (MOs) to which the user has access.
A privilege controls access to a particular function within the system. The ACI fabric manages access privileges at the managed object (MO) level. Every object holds a list of the privileges that can read from it and a list of the privileges that can write to it.
Example: ‘fabric-equipment’ is a privilege that controls access to all objects that correspond to equipment in the physical fabric. An object corresponding to equipment in the physical fabric, such as ‘eqptBoard,’ will have ‘fabric-equipment’ in its list of privileges.
The ‘eqptBoard’ object allows read-only access for the ‘fabric-equipment’ privilege. When a user is assigned a role such as ‘fabric-admin’ that contains the privilege ‘fabric-equipment,’ the user will have access to those equipment objects, including read-only access to the ‘eqptBoard’ object. - Privilege type: no access, read-only, or read-write, assigned for each role.
- Security Domain (one or multiples) which is a tag that identify the portions of the management information tree (MIT) that a user can access
A security domain is a tag associated with a certain subtree in the ACI MIT object hierarchy. For example, the default tenant “common” has a domain tag common. Similarly, the special domain tag all includes the entire MIT object tree. An administrator can assign custom domain tags to the MIT object hierarchy.
Example: If a virtual machine management (VMM) domain is tagged as a security domain, the users contained in the security domain can access the correspondingly tagged VMM domain. For example, if a tenant named solar is tagged with the security domain called sun and a VMM domain is also tagged with the security domain called sun, then users in the solar tenant can access the VMM domain according to their access rights.
For more details, please refer to: Cisco White paper
Remote user and TACACS Configuration: