Private VLAN Explained and Configuration(Step by Step Lab)
Contents
What is a Private VLAN
A private VLAN partitions the Ethernet broadcast domain of a VLAN into subdomains, allowing you to isolate the ports on the switch from each other. A subdomain consists of a primary VLAN and one or more secondary VLANs.
All VLANs in a private VLAN domain share the same primary VLAN. The secondary VLAN ID differentiates one subdomain from another. The secondary VLANs may either be isolated VLANs or community VLANs:
• Community VLAN: All ports within the community VLAN are able to communicate with
each other and the promiscuous port.
• Isolated VLAN: All ports within the isolated VLAN are unable to communicate with each
other but they can communicate with the promiscuous port.
• All other ports are able to communicate with the promiscuous port.
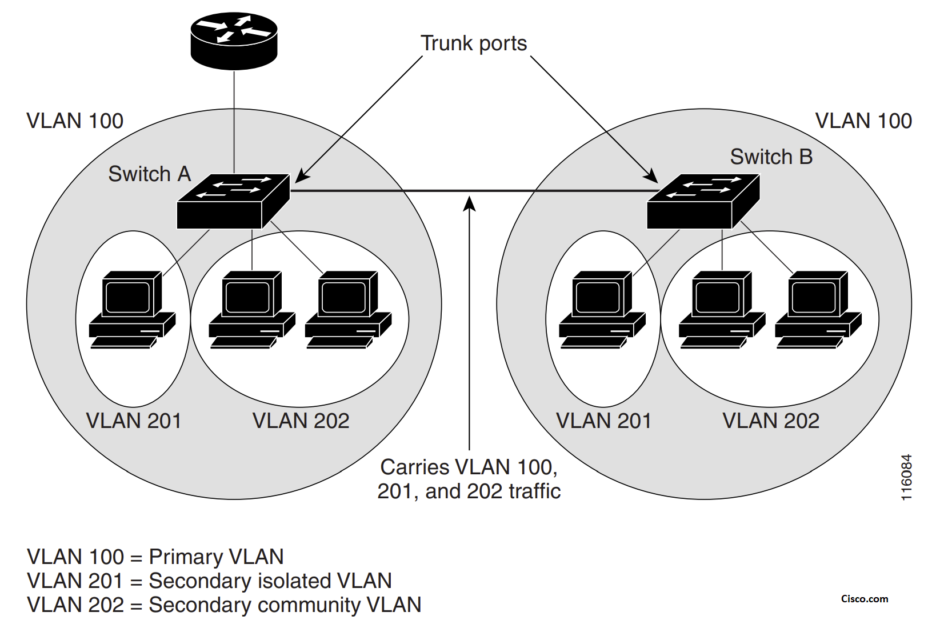
Private VLAN on Trunk:
As with regular VLANs, private VLANs can span multiple switches. A trunk port carries the primary
VLAN and secondary VLANs to a neighboring switch. The trunk port deals with the private VLAN as
any other VLAN.
Note
* Frames originating from a host in the secondary VLAN are tagged with the secondary (isolated or community) VLAN ID.
This way, beyond the Promiscious port, only Primary VLAN is visible.
In simple words, The traffic generated from secondary is Tagged with Secondary VLAN, but, the return traffic from Promiscious port to the hosts (members of secondary VLAN) is tagged with Primary.
Private VLANs and SVIs
- Layer 3 devices communicate with a private VLAN only through the primary VLAN and not through secondary VLANs. Configure Layer 3 VLAN SVIs only for primary VLANs. Do not configure Layer 3 VLAN interfaces for secondary VLANs. SVIs for secondary VLANs are inactive while the VLAN is configured as a secondary VLAN.
- If you try to create an SVI on a VLAN that is configured as a secondary VLAN, and the secondary
VLAN is already mapped at Layer 3, the SVI is not created, and an error is returned. If the SVI is
not mapped at Layer 3, the SVI is created, but it is automatically shut down.
- When the primary VLAN is associated with and mapped to the secondary VLAN, any configuration on the primary VLAN is propagated to the secondary VLAN SVIs. For example, if you assign an IP subnet to the primary VLAN SVI, this subnet is the IP subnet address of the entire private VLAN.
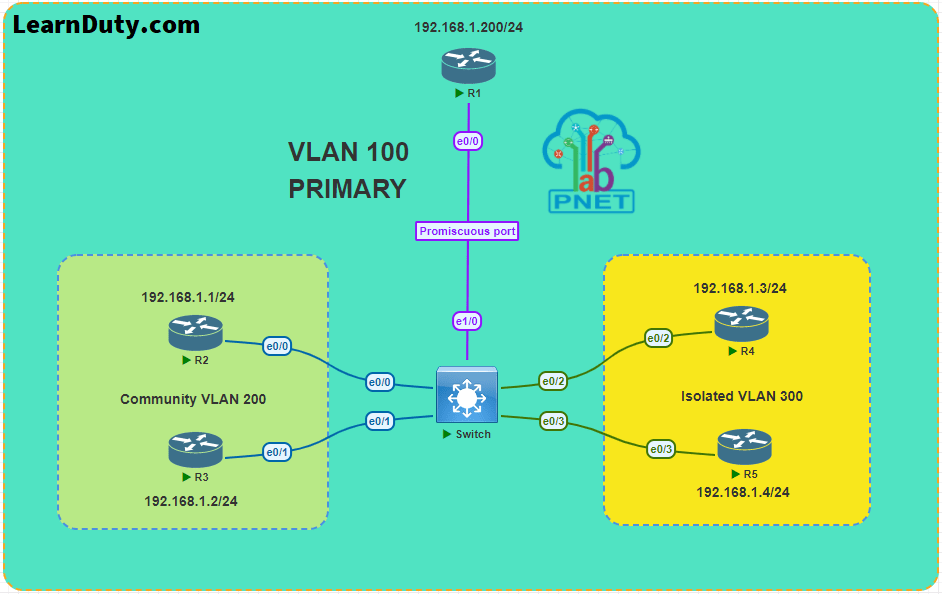
Private VLAN Configuration Example [Lab]
First of all, I have to mention that this lab is downloaded from PNETLAB Platform.
Lab Topology:
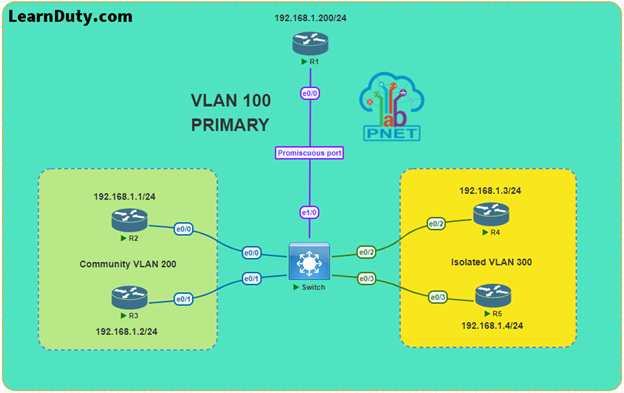
Now let’s dive into private VLAN configuration Step by Step:
Step-1: Configure Routers Interfaces and hostnames (pre-config):
R1:
***
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname R1
R1(config)#interface Ethernet0/0
R1(config-if)#ip address 192.168.1.200 255.255.255.0
R1(config-if)#
R2:
***
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#ho R2
R2(config)#!
R2(config)#interface Ethernet0/0
R2(config-if)#ip address 192.168.1.1 255.255.255.0
R2(config-if)#
R3:
***
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hos
Router(config)#hostname R3
R3(config)#interface Ethernet0/1
R3(config-if)#ip address 192.168.1.2 255.255.255.0
R4:
***
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname R4
R4(config)#interface Ethernet0/2
R4(config-if)#ip address 192.168.1.3 255.255.255.0
R4(config-if)#
R5:
***
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname R5
R5(config)#interface Ethernet0/3
R5(config-if)#ip address 192.168.1.4 255.255.255.0
Step-2: Configure Primary VLAN and Secondary VLANs (Community & Isolated):
Note: VTP transparent is a requirement on the switch for Private VLAN configuration.
On the switch:
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#vtp mode transparent
Setting device to VTP Transparent mode for VLANS.
1- Configure the Primary VLAN and associate it to its Private VLANs:
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#vlan 100
Switch(config-vlan)# private-vlan primary
Switch(config-vlan)# private-vlan association 200,300
2- Create Secondary VLANs:
- VLAN id 200 is a community VLAN:
Switch(config)#vlan 200
Switch(config-vlan)# private-vlan community- VLAN id 300 is an isolated VLAN:
Switch(config)#vlan 300
Switch(config-vlan)# private-vlan isolated
Step–3: Assign switch interfaces (endpoints) to their corresponding VLANs :
#Private VLAN 200:
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
#Private VLAN 200
Switch(config)#interface Ethernet0/0
Switch(config-if)#switchport private-vlan host-association 100 200
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#interface Ethernet0/1
Switch(config-if)#switchport private-vlan host-association 100 200
Switch(config-if)#switchport mode private-vlan host
#Private VLAN 300:
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
#Private VLAN 300
Switch(config-if)#!
Switch(config-if)#interface Ethernet0/2
Switch(config-if)#switchport private-vlan host-association 100 300
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#interface Ethernet0/3
Switch(config-if)#switchport private-vlan host-association 100 300
Switch(config-if)#switchport mode private-vlan host
Step-4: Configure the promiscuous Interface:
Configure the promiscuous interface and map it to Primary and secondary VLANs:
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#interface Ethernet1/0
Switch(config-if)#switchport private-vlan mapping 100 200,300
Switch(config-if)#switchport mode private-vlan promiscuous- Verifications:
Switch#show vlan private-vlan
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
100 200 community Et0/0, Et0/1, Et1/0
100 300 isolated Et0/2, Et0/3, Et1/0
Switch#show interfaces ethernet 0/1 switchport
Name: Et0/1
Switchport: Enabled
Administrative Mode: private-vlan host
Operational Mode: private-vlan host
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: 100 (VLAN0100) 200 (VLAN0200)
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 200 (VLAN0200)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
Switch#show interfaces ethernet 0/3 switchport
Name: Et0/3
Switchport: Enabled
Administrative Mode: private-vlan host
Operational Mode: private-vlan host
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: 100 (VLAN0100) 300 (VLAN0300)
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan:
100 (VLAN0100) 300 (VLAN0300)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Appliance trust: none
Tests and verifications
- The promiscuous Port should be able to ping all routers:
R1#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R1#
R1#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R1#ping 192.168.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R1#ping 192.168.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.4, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms- Hosts in the Community Vlan should be able to ping each other and the promiscuous port:
R2#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R2#ping 192.168.1.200
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.200, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms- Isolated VLAN hosts can ping only Promiscious ports:
R4#ping 192.168.1.200
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.200, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
R4#ping 192.168.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.4, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
R4#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
That’s all about Private VLAN, hope you enjoyed it, thanks for PNETLAB again, and see you very Soon.

![OSPF DR and BDR Election Explained [with Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-33.png?v=1647900046)
![OSPF Neighbor Adjacency Requirements [With Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-23-418x450.png?v=1647900064)
![BGP Route Reflector [Explained & Configuration]](https://learnduty.com/wp-content/uploads/2022/02/image-79-531x450.png?v=1647900109)
![Cisco Catalyst 9000 Switches Upgrade [Step by step]](https://learnduty.com/wp-content/uploads/2022/02/image-54.png?v=1647900155)
![L2 Interface Policy – Per Port VLAN in Cisco ACI [Explained]](https://learnduty.com/wp-content/uploads/2022/02/image-42.png?v=1647900173)