Extended Access List Configuration [Step by Step]
![Extended Access List Configuration [Step by Step]](https://learnduty.com/wp-content/uploads/2021/07/word-image-114.png)
Packet Tracer Topology
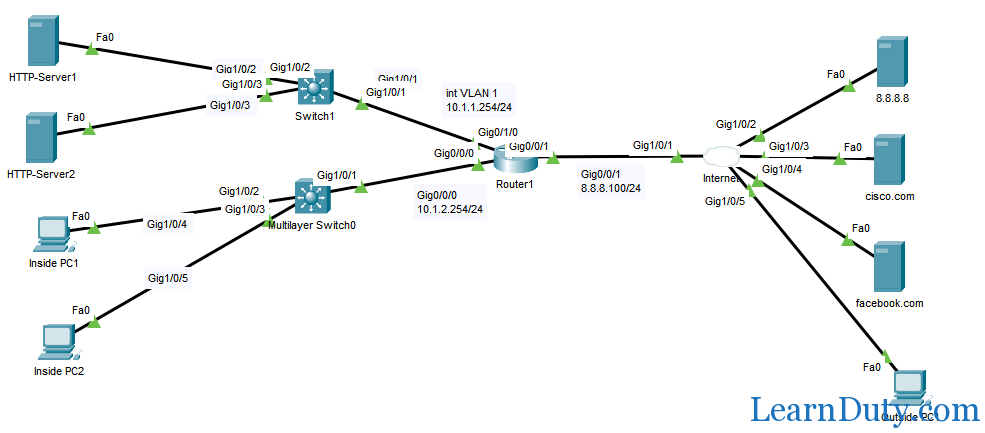
Contents
ACL Rules to implement
Restrict traffic internally using Router1 as follows:
– Use access-list number 100
- Inside PC1 can only access the HTTP server 1 using HTTP on subnet 10.1.1.0/24
- Inside PC2 can only access the HTTP server 2 using HTTPS on subnet 10.1.1.0/24
- No other PCs or servers on subnet 10.1.2.0/24 can access subnet 10.1.1.0/24
- Hosts on subnet 10.1.2.0/24 can access any other network
I- Extended Access-list configuration:
For Extended ACL configuration, we have two options:
- Numbered ACL
- Named ACL
Numbered ACLs Configurations:
On Router1, we will configure the following ACLs:
conf t
access-list 100 permit tcp host 10.1.2.101 host 10.1.1.100 eq www
access-list 100 permit tcp host 10.1.2.102 host 10.1.1.101 eq 443
access-list 100 deny ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255
access-list 100 permit ip 10.1.2.0 0.0.0.255 any
The equivalent Named ACL for the configuration above is:
Named ACLs Configurations
conf t
ip access-list extended branches
10 permit tcp host 10.1.2.101 host 10.1.1.100 eq www
20 permit tcp host 10.1.2.102 host 10.1.1.101 eq 443
30 deny ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255
40 permit ip 10.1.2.0 0.0.0.255 anyVerification:
Router1#show access-lists
Extended IP access list 100
10 permit tcp host 10.1.2.101 host 10.1.1.100 eq www
20 permit tcp host 10.1.2.102 host 10.1.1.101 eq 443
30 deny ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255
40 permit ip 10.1.2.0 0.0.0.255 any
Delete a rule in an Access-List (without deleting the whole Access List):
In order to delete a rule in an Access List without deleting the whole Access, you need to enter under access-list configuration mode and perform no followed with rule id that you will delete.
Router1(config)#ip access-list extended 100
Router1(config-ext-nacl)#no 40
Router1(config-ext-nacl)#end
Router1#
%SYS-5-CONFIG_I: Configured from console by console
Router1#show access-lists
Extended IP access list 100
10 permit tcp host 10.1.2.101 host 10.1.1.100 eq www
20 permit tcp host 10.1.2.102 host 10.1.1.101 eq 443
30 deny ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255
II- Configure Inbound interface in the router to apply the access-list
Router1>en
Router1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router1(config)#int gigabitEthernet 0/0/0
Router1(config-if)#ip access-group 100 in
Router1(config-if)#end
%SYS-5-CONFIG_I: Configured from console by console
III- Verifications
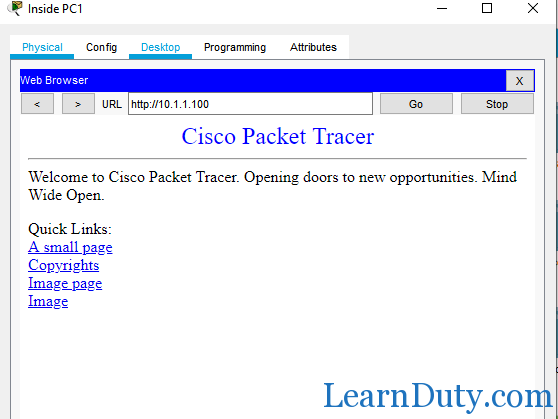
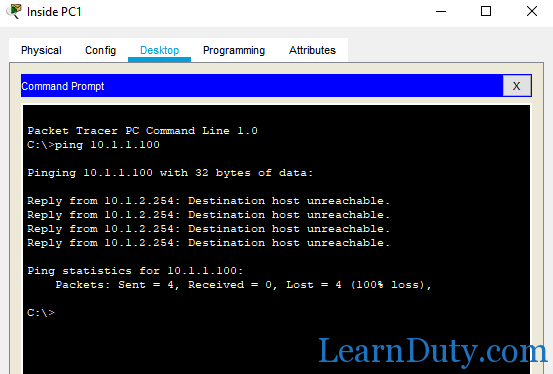
So, PC1 can access server 1 10.1.1.100 via HTTP (port 80) as configured in the access-list but it can’t ping it cause of the access-list 30 (30 deny ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255):
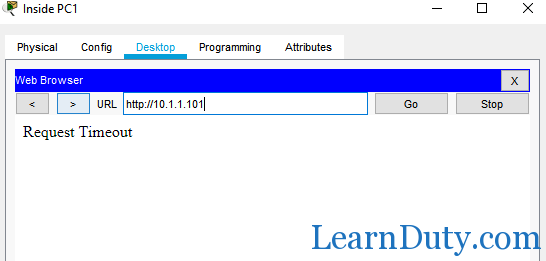
* Also, PC1 cannot access server 2 via HTTP which is expected:
Let’s test if inside PC2 can access servers:
so it can access PC2 cannot access server1:
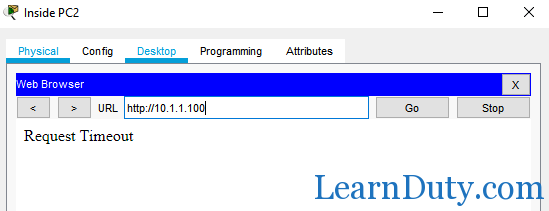
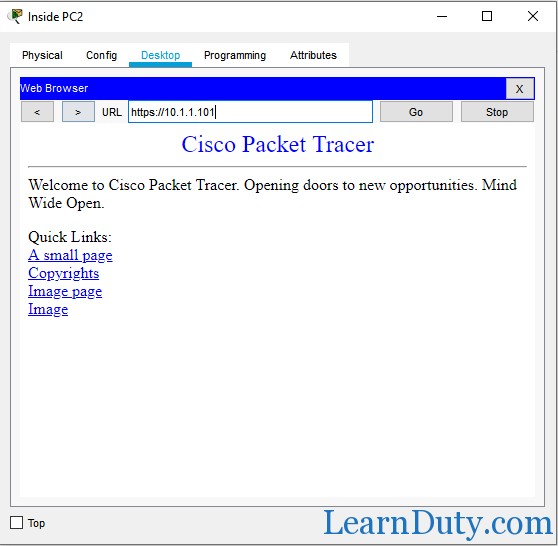
but it can access server2 via HTTPS, as described in the access-list:
20 permit tcp host 10.1.2.102 host 10.1.1.101 eq 443:
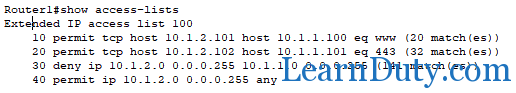
We can see in the router that the access lists are matched when we performed the test above:
Also, PC1 (10.1.2.101) can access cisco.com, because that match the 40 rule:
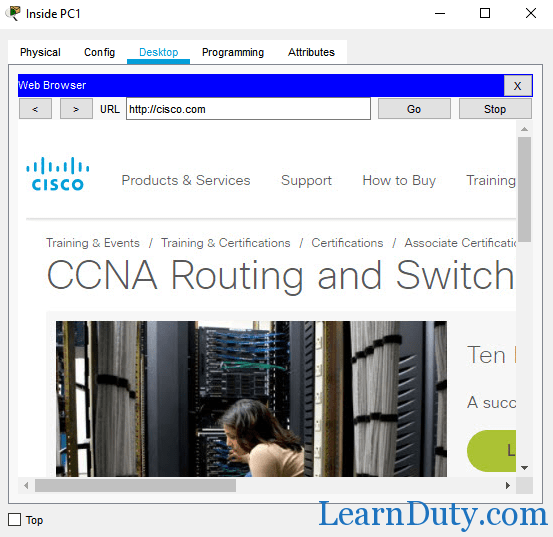
Let’s check the matched access-list:
Router1#show access-lists
Extended IP access list 100
10 permit tcp host 10.1.2.101 host 10.1.1.100 eq www (20 match(es))
20 permit tcp host 10.1.2.102 host 10.1.1.101 eq 443 (32 match(es))
30 deny ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255 (145 match(es))
40 permit ip 10.1.2.0 0.0.0.255 any (76 match(es))We can see that the last access-list was matched because we are accessing cisco.com from 10.1.2.100 (we can access any network from 10.1.2.0/24 network except the 10.1.1.0 network because it was blocked by the previous access-list (order matters here))
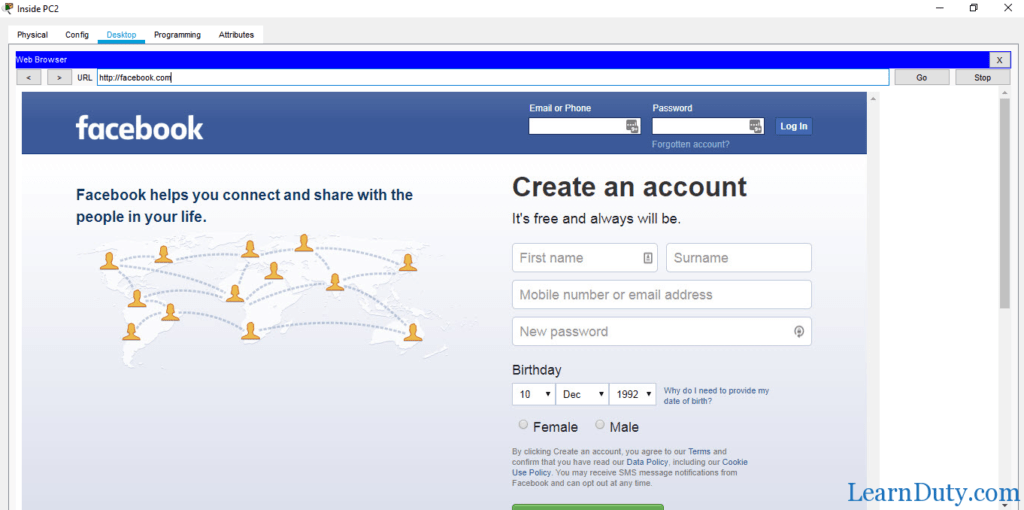
also, PC1 and PC2 can access facebook.com for example because that match the last rule in the access list:

![OSPF DR and BDR Election Explained [with Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-33.png?v=1647900046)
![OSPF Neighbor Adjacency Requirements [With Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-23-418x450.png?v=1647900064)
![BGP Route Reflector [Explained & Configuration]](https://learnduty.com/wp-content/uploads/2022/02/image-79-531x450.png?v=1647900109)
![Cisco Catalyst 9000 Switches Upgrade [Step by step]](https://learnduty.com/wp-content/uploads/2022/02/image-54.png?v=1647900155)
![L2 Interface Policy – Per Port VLAN in Cisco ACI [Explained]](https://learnduty.com/wp-content/uploads/2022/02/image-42.png?v=1647900173)