Virtual Port Channel (vPC) Peer-gateway Explained [Configuration example]
![Virtual Port Channel (vPC) Peer-gateway Explained [Configuration example]](https://learnduty.com/wp-content/uploads/2022/12/image-33.png)
The following post consists of some notes from the Cisco vPC document.
What is vPC Peer-Gateway
vPC PeerGateway allows a vPC peer device to act as the active gateway for packets addressed to the other peer device router MAC. It keeps the forwarding of traffic local to the vPC peer device and avoids the use of the peer link (by not bridging the traffic to the other vPC peer device).
Use case example:
A common use case that needs vPC peer gateway is devices that do not perform ARP:
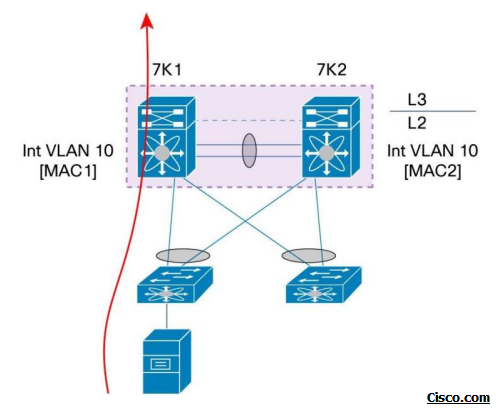
Let’s assume NAS device receives its first packet from vPC peer device 7K2. In this case, it will use MAC address of interface VLAN 10 on 7K2 as the default gateway MAC address. All routed traffic sent by NAS device need then to reach 7K2 in order to be routed correctly (L3 traffic destined out of vPC domain or inter-VLAN traffic).
For interVLAN traffic, there is a risk to hit the vPC loop avoidance issue: NAS device send routed traffic, the access switch hashes the traffic in the direction to 7K1, 7K1 has to bridge the traffic over vPC peer-link because 7K2 MAC address (more exactly MAC address of interface VLAN 10) is the L2 destination of this traffic. Now, if traffic needs to exit out a vPC member port, it will be dropped in hardware because of vPC loop avoidance rule.
By enabling vPC Peer-Gateway functionality, each vPC peer device will replicate locally the MAC address of the interface VLAN defined on the other vPC peer device with the G flag (Gateway flag).
vPC peer-gateway Configuration Example
Let’s test the vPC peer-gateway feature:
Topology:
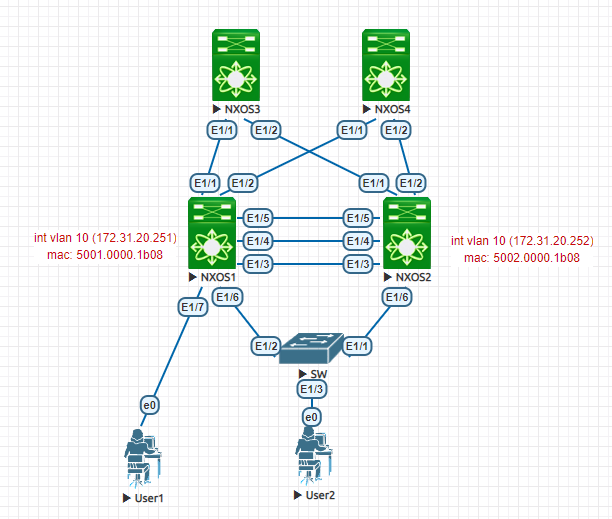
1- Without vPC peer-gateway:
On the NX01 mac address table, we can see the interface VLAN MAC of NX02 (5002.0000.1b08) associated with the peer-link interface, which means if NX01 gets a frame with a destination MAC of 5002.0000.1b08, it will be forwarded to the peer via the peer link.
NX01# show mac address-table
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
+ 1 0050.0000.0600 dynamic 0 F F Po10
* 1 0050.0000.0700 dynamic 0 F F Eth1/7
* 10 0050.0000.0600 dynamic 0 F F Po10
+ 1 5003.0000.1b08 dynamic 0 F F vPC Peer-Link
+ 1 5004.0000.1b08 dynamic 0 F F vPC Peer-Link
G - 5001.0000.1b08 static - F F sup-eth1(R)
G 10 5001.0000.1b08 static - F F sup-eth1(R)
* 10 5002.0000.1b08 static - F F vPC Peer-Link(R)
Same on the NX02 side (5001.0000.1b08 via the peer-link):
NX02# show mac address-table
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
* 1 5003.0000.1b08 dynamic 0 F F Eth1/1
+ 10 0050.0000.0600 dynamic 0 F F Po10
+ 1 0050.0000.0700 dynamic 0 F F vPC Peer-Link
+ 1 5004.0000.1b08 dynamic 0 F F vPC Peer-Link
* 10 5001.0000.1b08 static - F F vPC Peer-Link(R)
G - 5002.0000.1b08 static - F F sup-eth1(R)
G 10 5002.0000.1b08 static - F F sup-eth1(R)
1- With vPC peer-gateway:
Apply the following configuration under the vPC domain on both vPC devices:
vpc domain 1
peer-gatewayLet’s check the difference, we can see that a Flag is added to the MAC address of the NX02 interface VLAN (5002.0000.1b08), this will allow each vPC peer to forward the packets which have the destination MAC of the peer device locally without bridging it to the peer via peer link.
NX01# show mac address-table
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
* 1 0050.0000.0700 dynamic 0 F F Eth1/7
* 1 5003.0000.1b08 dynamic 0 F F Eth1/1
* 1 5004.0000.1b08 dynamic 0 F F Eth1/2
* 10 0050.0000.0600 dynamic 0 F F Po10
G - 5001.0000.1b08 static - F F sup-eth1(R)
G 10 5001.0000.1b08 static - F F sup-eth1(R)
G 10 5002.0000.1b08 static - F F vPC Peer-Link(R)
![Explore The BGP Path Selection Attributes [Explained with Labs]](https://learnduty.com/wp-content/uploads/2022/07/image-28-800x450.png)