Layer 2 Interface Tagging & Trunking and SVI Auto-state
Contents
Access and Trunk Ports
A Layer 2 port can be configured as:
- An access port: can have only one VLAN configured on the port.
- A trunk port can have two or more VLANs configured on the port.
Note: for Nexus 7k, all ports in the same trunk must be in the same VDC, and trunk ports cannot carry VLANs from different VDCs.
A Layer 2 interface can function as either an access port or a trunk port; it cannot function as both port types simultaneously.
Trunk port
- A trunk is a point-to-point link between the switch and another networking device. Trunks carry the traffic of multiple VLANs over a single link and allow you to extend VLANs across an entire network.
IEEE 802.1Q encapsulation
- To deliver the traffic on a trunk port with several VLANs, the device uses the IEEE 802.1Q encapsulation, or tagging method that uses a tag that is inserted into the frame header.
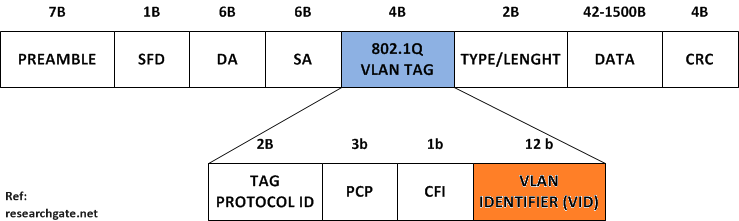
- This tag carries information about the specific VLAN (VLAN IDENTIFIER, VID) to which the frame belong.
- This method allows packets that are encapsulated for several different VLANs to traverse the same port and maintain traffic separation between the VLANs.
Native VLAN IDs for Trunk ports
A trunk port can carry untagged packets simultaneously with the 802.1Q tagged packets. When you assign a default port VLAN ID to the trunk port, all untagged traffic travels on the default port VLAN ID for the trunk port, and all untagged traffic is assumed to belong to this VLAN: This VLAN is referred to as the native VLAN.
–> Native VLAN traffic is sent untagged on the trunk ports
Note:
- Native VLAN ID numbers must match on both ends of the trunk.
- If you do not configure a native VLAN ID, the trunk port uses the default VLAN.
Tagging Native VLAN Traffic
All packets that enter the device with an 802.1Q tag that matches the value of the native VLAN on the trunk are stripped out of any tagging and egress the trunk port as untagged packets. This situation can cause problems because you may want to retain the tagging on packets on the native VLAN for the trunk port.
Impact of configuring “vlan dot1q tag native” on trunk ports:
Egress: Configuring “vlan dot1q tag native“ will cause all frames being sent out a trunk port to be tagged, ignoring the native VLAN.
Ingress: Configuring “vlan dot1q tag native“ will drop all untagged packets on the trunk ports and to retain the tagging of packets entering the device with 802.1Q value that is equal to that of the native VLAN ID.
Note: All control traffic still passes on the native VLAN. This configuration is global: trunk ports on the device either do or do not retain the tagging for the native VLAN.
Global and port level configuration:
- Global configuration: “vlan dot1q tag native“, this will apply to all trunk port in a device.
- Port level configuration: From Cisco NX-OS Release 6.2(10), you can specify whether control and data packets are tagged or untagged using the switchport trunk native vlan tag command at the port level.
Example: Under trunk port you configure: “switchport trunk native vlan tag exclude control“
it imply that data packets are tagged and control packets are untagged.
which means that Native vlan tagging was only applied on data packet and control plane packet were excluded, as a result, the default native VLAN behavior is applied on control plane (which is sending as untagged on trunk port).
Access port
When you configure a port in access mode, you can specify which VLAN will carry the traffic for that interface. If you do not configure the VLAN for a port in access mode, or an access port, the interface carries traffic for the default VLAN (VLAN1).
If an access port receives a packet with an 802.1Q tag in the header other than the configured access VLAN value, that port drops the packet without learning its MAC source address.
SVI Auto-state
In Cisco NX-OS, a switch virtual interface (SVI) represents a logical interface between the bridging function and the routing function of a VLAN in the device
The operational state of this interface is governed by the state of the various ports in its corresponding VLAN.
The following behavior is referred to as Auto-state:
- An SVI interface on a VLAN comes up when at least one port in that VLAN is in the Spanning Tree Protocol (STP) forwarding state.
- Same way, this interface goes down when the last STP forwarding port goes down or goes to another STP state.
SVI Autostate Exclude
As mentioned previously , By default, the SVI goes to the down state when all the ports in the VLAN go down.
SVI autostate exclude feature can exclude a port or port-channel from the calculation while defining the status of the SVI (either UP or DOWN) even if the port belong to the same VLAN for the SVI.
For example:
N7K-SW(config)# interface ethernet 1/20
N7K-SW(config-if)# switchport
N7K-SW(config-if)# switchport autostate exclude vlan 50Let’s say interface ethernet 1/20 is part of VLAN 50 (either access or trunk), if you configure an SVI for VLAN 50, the calculation will check:
- If the VLAN exist and active in the VLAN database
- minimum 1 port for this VLAN is up and in spanning tree forwarding state
When you configure the “autostate exclude” under eth1/20 , the port eth1/20 will not considered while defining the status of the SVI (in our example SVI 50).
So, even if you 1/20 is UP and in forwarding state (at the same time, there is no other ports and port-channel in this VLAN up and forwarding), the SVI will be NOT up, because simply the interface eth1/20 which is UP (forwarding status) wasn’t taken into account while calculating the UP/DOWN status for the SVI.
You can apply the exclude for all VLAN for a specific port:
N7K-SW(config)# interface ethernet 1/20
N7K-SW(config-if)# switchport
N7K-SW(config-if)# switchport autostate exclude
SVI Autostate Disable
SVI Autostate Disable feature keeps an SVI up even if no interface is up in the corresponding VLAN. You can configure this feature for the system (for all SVIs) or for an individual SVI.
In NXOS, the auto-state Disable can be apply globally or per SVI:
- Globally, you alter the default behavior via command:
N7K-SW(config)# system default interface-vlan no autostate- On specific SVI, you can disable SVI Auto-state:
N7K-SW(config)# interface vlan50
N7K-SW(config-if)# no autostate
![Explore The BGP Path Selection Attributes [Explained with Labs]](https://learnduty.com/wp-content/uploads/2022/07/image-28-800x450.png)