Cisco SD-Access Architecture and Components
Contents
SD-Access Solution Components
The SD-Access solution is provided through a combination of:
- Cisco DNA Center,
- The Identity Services Engine (ISE),
- and wired and wireless device platforms which have fabric functionality: the wired and wireless device platforms are utilized to create the elements of a fabric site. This section describes the functionality of the remaining two components for SD-Access: Cisco DNA Center and the Identity Services Engine.
Cisco DNA Center (DNAC)
Cisco DNA Center software, including the SD-Access application package, run on Cisco DNA Center hardware appliance. The appliance is available in form factors sized to support not only the SD-Access application but also network Assurance and Analytics, Software image management (SWIM), Wide-Area Bonjour, and new capabilities as they are available.
Cisco DNA Center is the centralized manager running a collection of application and services powering the Cisco Digital Network Architecture (Cisco DNA). Cisco DNA begins with the foundation of a digital-ready infrastructure that includes routers, switches, access-points, and Wireless LAN controllers. Automation, Analytics, Visibility, and management of the Cisco DNA network is enabled through Cisco DNA Center Software.
Identity Services Engine (ISE)
Cisco Identity Services Engine (ISE) is a secure network access platform enabling increased management awareness, control, and consistency for users and devices accessing an organization’s network. ISE is an integral and mandatory component of SD-Access for implementing network access control policy. ISE performs policy implementation, enabling dynamic mapping of users and devices to scalable groups, and simplifying end-to-end security policy enforcement. Within ISE, users and devices are shown in a simple and flexible interface. ISE integrates with Cisco DNA Center by using Cisco Platform Exchange Grid (pxGrid) and REST APIs (Representational State Transfer Application Programming Interfaces) for endpoint event notifications and automation of policy configurations on ISE.
The SD-Access solution integrates Cisco TrustSec by supporting end-to-end group-based policy with Scalable Group Tags (SGTs). Scalable Group Tags are a metadata value that is transmitted in the header of fabric-encapsulated packets. While SGTs are administered by Cisco ISE through the tightly integrated REST APIs, Cisco DNA Center is used as the pane of glass to manage and create SGTs and define their policies. Group and policy services are driven by ISE and orchestrated by Cisco DNA Center’s policy authoring workflows.
ISE Personas
Personas are simply the services and specific feature sets provided by a given ISE node.
ISE supports standalone and distributed deployment models. Multiple, distributed nodes can be deployed together to provide failover resiliency and scale. The range of deployment options allows support for hundreds of thousands of endpoint devices. Minimally, a basic two-node ISE deployment is recommended for SD-Access single-site deployments with each ISE node running all services (personas) for redundancy.
SD-Access fabric nodes send authentication requests to the Policy Services Node (PSN) service persona running in ISE. In the case of a standalone deployment, the PSN persona is referenced by a single IP address. An ISE distributed model uses multiple, active PSN personas, each with a unique address.
SD-Access Architecture
There are four key technologies, that make up the SD-Access solution, each performing distinct activities in different network planes of operation: control plane, data plane, policy plane, and management plane.
● Control Plane: Messaging and communication protocol between infrastructure devices in the fabric. In SD-Access the control plane is based on LISP (Locator/ID Separation Protocol)
● Data Plane: Encapsulation method used for the data packets. The data plane is based on VXLAN (Virtual Extensible LAN)
● Policy Plane: Used for security and segmentation. The policy plan is based on Cisco TrustSec
● Management Plane—Orchestration, assurance, visibility, and management. The management plane is enabled and powered by Cisco DNA Center.
Underlay Network:
The underlay network is defined by the physical switches and routers that are used to deploy the SD-Access network. All network elements of the underlay must establish IP connectivity via the use of a routing protocol. Instead of using arbitrary network topologies and protocols, the underlay implementation for SD-Access uses a well-designed Layer 3 foundation inclusive of the campus edge switches which is known as a Layer 3 Routed Access design.
In SD-Access, the underlay switches (edge nodes) support the physical connectivity for users and endpoints. However, end-user subnets and endpoints are not part of the underlay network—they are part of the automated overlay network.
Overlay Network:
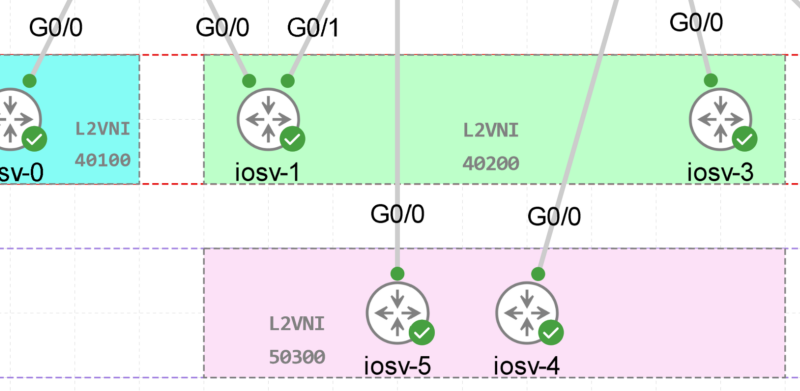
An overlay network is created on top of the underlay network through virtualization (virtual networks). The data plane traffic and control plane signaling are contained within each virtualized network, maintaining isolation among the networks and an independence from the underlay network. Multiple overlay networks can run across the same underlay network through virtualization. In SD-Access, the user-defined overlay networks are provisioned as a virtual routing and forwarding (VRF) instances that provide separation of routing tables.
SD-Access allows for the extension of Layer 2 and Layer 3 connectivity across the overlay through the services provided by through LISP.

![Explore The BGP Path Selection Attributes [Explained with Labs]](https://learnduty.com/wp-content/uploads/2022/07/image-28-800x450.png)