Spanning Tree (STP) Features Explained
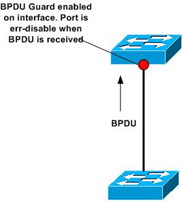
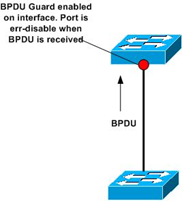
BPDU Guard:
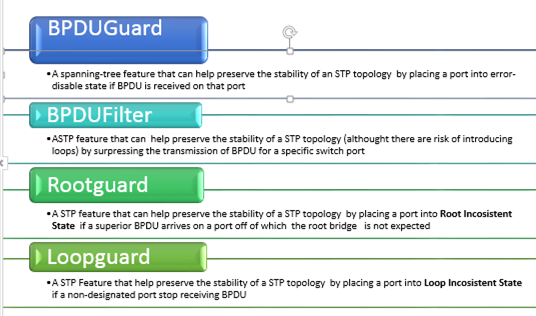
The STP PortFast BPDU guard enhancement allows network designers to enforce the STP domain borders and keep the active topology predictable. The devices behind the ports that have STP PortFast enabled are not able to influence the STP topology. At the reception of BPDUs, the BPDU guard operation disables the port that has PortFast configured. The BPDU guard transitions the port into the err-disable state, and a message appears on the console.
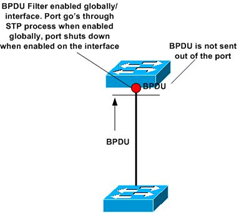
BPDU Filter
The BPDU filtering feature can be globally enabled on the switch or can be enabled per interface, but the feature operates with some differences.
At the global level, you can enable BPDU filtering on Port Fast-enabled STP ports by using the spanning-tree portfast bpdufilter default global configuration command. This command prevents interfaces that are in a Port Fast-operational state from sending or receiving BPDUs. The interfaces still send a few BPDUs at link-up before the switch begins to filter outbound BPDUs. You should globally enable BPDU filtering on a switch so that hosts connected to these ports do not receive BPDUs. If a BPDU is received on a Port Fast-enabled STP port, the interface loses its Port Fast-operational status, and BPDU filtering is disabled.
At the interface level, you can enable BPDU filtering on any STP port by using the spanning-tree bpdufilter enable interface configuration command without also enabling the Port Fast feature. This command prevents the interface from sending or receiving BPDUs.
BPDUfilter on the other hand just filters BPDUs in both directions, which effectively disables STP on the port.Bpdu filter will prevent inbound and outbound bpdu but will remove portfast state on a port if a bpdu is received.Enabling BPDU filtering on an interface is the same as disabling spanning tree on it and can result in spanning-tree loops.
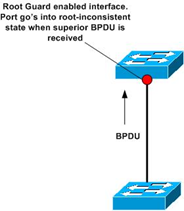
Root Guard
Root guard does not allow the port to become a STP root port, so the port is always STP-designated. If a better BPDU arrives on this port, root guard does not take the BPDU into account and elect a new STP root. Instead, root guard puts the port into the root-inconsistent STP state which is equal to a listening state. No traffic is forwarded across this port
.
Below is an example of where to configure Root Guard on the ports. Notice that Root Guard is always configure on designated ports.
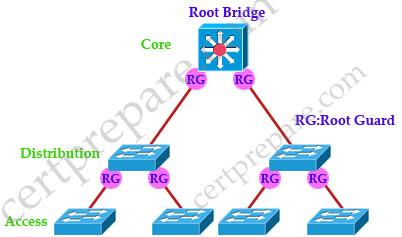
To configure Root Guard use this command:
Switch(config-if)# spanning-tree guard root
Loop Guard
The STP loop guard feature provides additional protection against Layer 2 forwarding loops (STP loops). An STP loop is created when an STP blocking port in a redundant topology erroneously transitions to the forwarding state. This usually happens because one of the ports of a physically redundant topology (not necessarily the STP blocking port) no longer receives STP BPDUs. In its operation, STP relies on continuous reception or transmission of BPDUs based on the port role. The designated port transmits BPDUs, and the non-designated port receives BPDUs.
When one of the ports in a physically redundant topology no longer receives BPDUs, the STP conceives that the topology is loop-free. Eventually, the blocking port from the alternate or backup port becomes designated and moves to a forwarding state. This situation creates a loop.
The loop guard feature makes additional checks. If BPDUs are not received on a non-designated port, and loop guard is enabled, that port is moved into the STP loop-inconsistent blocking state, instead of the listening / learning / forwarding state. Without the loop guard feature, the port assumes the designated port role. The port moves to the STP forwarding state and creates a loop.
* When implementing Loop Guard, you should be aware of the following implementation guidelines:
- Loop Guard cannot be enabled on a switch that also has Root Guard enabled.
- Loop Guard does not affect Uplink Fast or Backbone Fast operation.
- Loop Guard must be enabled on point-to-point links only.
- Loop Guard operation is not affected by the Spanning Tree timers.
- Loop Guard cannot actually detect a unidirectional link.
- Loop Guard cannot be enabled on Port Fast or Dynamic VLAN ports.
You configure the Loop Guard feature on a per-port basis, although the feature blocks inconsistent ports on a per-VLAN basis. For example, on a trunk port, if BPDUs are not received for only one particular VLAN, the switch blocks only that VLAN (that is, moves the port for that VLAN to the loop-inconsistent STP state).
In the case of an Ether Channel interface, the channel status goes into the inconsistent state for all the ports belonging to the channel group for the particular VLAN not receiving BPDUs. Enable the Loop Guard feature on all non-designated ports, and not just for blocking ports.
More precisely, Loop Guard should be enabled on root and alternative ports for all possible combinations of active topologies. Before enabling Loop Guard, however, consider all possible failover scenarios.
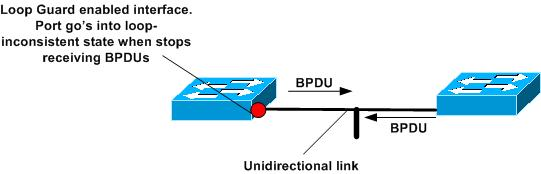
Recovery:
Once the BPDU is received on a port in a loop-inconsistent STP state, the port transitions into another STP state. According to the received BPDU, this means that the recovery is automatic and intervention is not necessary.
Summary of STP Features:
Reference:
nocsma.wordpress.com/2018/03/06/bpdu-guard-bpdu-filter-root-guard-loop-guard-udld/
https://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10586-65.html
https://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10596-84.html


![OSPF DR and BDR Election Explained [with Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-33.png?v=1647900046)
![OSPF Neighbor Adjacency Requirements [With Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-23-418x450.png?v=1647900064)
![OSPF Neighbor States Explained [Step by Step]](https://learnduty.com/wp-content/uploads/2022/03/image-13.png?v=1647900076)
![OSPF Area Types Explained and Configuration [Demystified]](https://learnduty.com/wp-content/uploads/2022/03/image-8.png?v=1647900083)