Cisco ACI Taboo Contract Explained and Configuration Example
ACI Contract overview
In detail, contracts are comprised of the following items:
- Name: All contracts that are consumed by a tenant must have different names (including contracts created under the common tenant or the tenant itself).
- Subjects: A group of filters for a specific application or service.
- Filters: Used to classify traffic based upon layer 2 to layer 4 attributes (such as Ethernet type, protocol type, TCP flags and ports).
- Actions: Action to be taken on the filtered traffic. The following actions are supported:
- Permit the traffic (regular contracts, only)
- Mark the traffic (DSCP/CoS) (regular contracts, only)
- Redirect the traffic (regular contracts, only, through a service graph)
- Copy the traffic (regular contracts, only, through a service graph or SPAN)
- Block the traffic (taboo contracts)With Cisco APIC Release 3.2(x) and switches with names that end in EX or FX, you can alternatively use a subject Deny action or Contract or Subject Exception in a standard contract to block traffic with specified patterns.
- Log the traffic (taboo contracts and regular contracts)
Taboo contract
While the normal processes for ensuring security still apply, the ACI policy model aids in assuring the integrity of whatever security practices are employed. In the ACI policy model approach, all communications must conform to these conditions:
- Communication is allowed only based on contracts, which are managed objects in the model. If there is no contract, inter-EPG communication is disabled by default.
- No direct access to the hardware; all interaction is managed through the policy model.
The Taboo contract is used to deny and log traffic destined to a specific EPG. The Taboo contract has priority 5, which is higher than regular contracts.
Taboo contracts can be used to deny specific traffic that is otherwise allowed by contracts. The traffic to be dropped matches a pattern (such as, any EPG, a specific EPG, or traffic matching a filter). Taboo rules are unidirectional, denying any matching traffic coming toward an EPG that provides the contract.
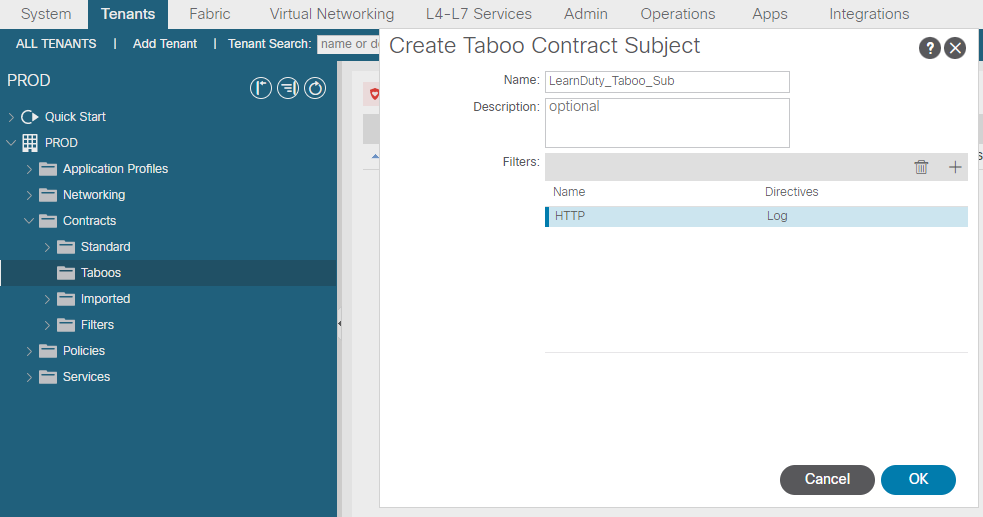
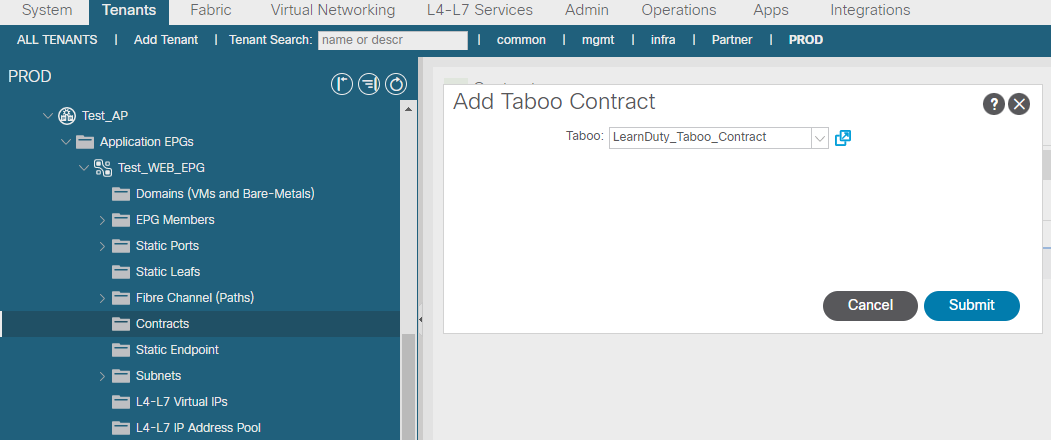
Taboo contract Configuration Example
Navigate to: Tenant > Security > Contracts > Taboos.
- In theDirectives drop-down list, choose log.