VLAN configuration Cisco IOS switches & Router configuration
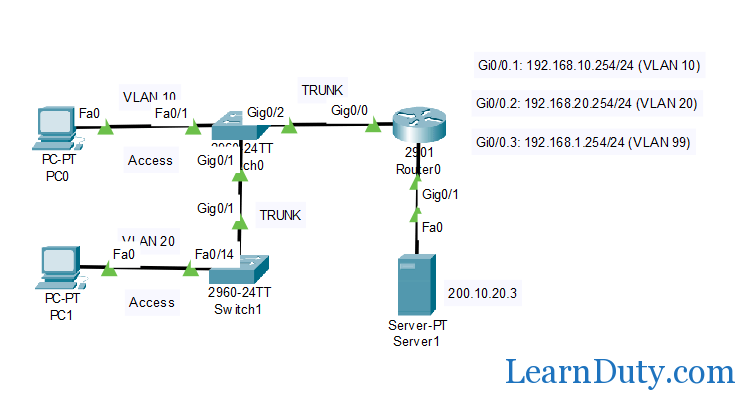
Topology:
Step 1: configuring default gateway on both switches:
Switch>en
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#vlan 99
Switch(config-vlan)#exit
Switch(config)#int vlan 99
Switch(config-if)#
%LINK-5-CHANGED: Interface Vlan99, changed state to up
Switch(config-if)#ip add
Switch(config-if)#ip address 192.168.1.1 255.255.255.0
Switch(config-if)#no sh
Switch(config-if)#exit
Switch(config)#ip default-gateway 192.168.1.254
Switch(config)#exit
Switch#
%SYS-5-CONFIG_I: Configured from console by console
Switch#cop
Switch#copy r
Switch#copy running-config s
Switch#copy running-config st
Switch#copy running-config startup-config
Destination filename [startup-config]?
Building configuration…
[OK]
Step 2: configuring VLANs on switches:
switch0(config)#vlan 10
switch0(config-vlan)#name Compt
switch0(config-vlan)#exit
switch0(config)#vlan 20
switch0(config-vlan)#name Radio
switch0(config-vlan)#exit
switch0(config)#vlan 99
switch0(config-vlan)#name man
switch0(config-vlan)#name mgmt
switch0(config-vlan)#exit
switch0(config)#vlan 100
switch0(config-vlan)#name NATIVE
switch0(config-vlan)#exit
Verification:
switch1#show vlan
VLAN Name Status Ports
—- ——————————– ——— ——————————-
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
10 compt active
20 radio active
99 mgmt active
100 NATIVE active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
Step 3: Configuration of access and trunk ports:
1- Access port for vlan 10 :
switch0(config)#int range f0/1-12
switch0(config-if-range)#switchport mode access
switch0(config-if-range)#switchport access vlan 10
switch0(config-if-range)#spanning-tree portfast
2- Access port for vlan 20 :
switch0(config)#int range f0/13-23
switch0(config-if-range)#switchport mode access
switch0(config-if-range)#switchport access vlan 20
switch0(config-if-range)#spanning-tree portfast
%Warning: portfast should only be enabled on ports connected to a single
host. Connecting hubs, concentrators, switches, bridges, etc… to this
interface when portfast is enabled, can cause temporary bridging loops.
3- Verification of access ports:
switch1#show vlan
VLAN Name Status Ports
—- ——————————– ——— ——————————-
1 default active Fa0/24, Gig0/1, Gig0/2
10 compt active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
20 radio active Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23
99 mgmt active
100 NATIVE active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
3- Trunk port configuration:
- on switch0 and switch1:
switch0(config)#int gi0/1
switch0(config-if)#switchport mode trunk
switch0(config-if)#switchport trunk native vlan 100
switch0(config-if)#exit
- Only on switch0:
switch0(config)#int gi0/2
switch0(config-if)#switchport mode trunk
switch0(config-if)#switchport trunk native vlan 100
Verification des interfaces trunk:
switch0#show interfaces switchport
Name: Gig0/1
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 100 (NATIVE)
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: All
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Unknown unicast blocked: disabled
Unknown multicast blocked: disabled
Appliance trust: none
—————————————-
Name: Gig0/2
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: down
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 100 (NATIVE)
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: All
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Unknown unicast blocked: disabled
Unknown multicast blocked: disabled
Appliance trust: none
switch0#show interfaces trunk
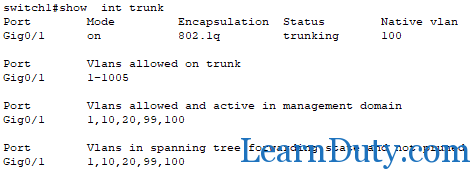
Dynamic trunking protocol (DTP) verification:
switch0#show dtp
Global DTP information
Sending DTP Hello packets every 30 seconds
Dynamic Trunk timeout is 300 seconds
1 interfaces using DTP
Step 4 : Gateways configuration on router:
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int gigabitEthernet 0/0
Router(config-if)#no ip address
Router(config-if)#no sh
%LINK-5-CHANGED: Interface GigabitEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to upRouter(config-if)#exit
Router(config)#interface gigabitEthernet 0/0.1
Router(config-subif)#encapsulation dot1Q 10
Router(config-subif)#ip address 192.168.10.254 255.255.255.0
Router(config-subif)#exit
Router(config)#int gi0/0.2
Router(config-subif)#
%LINK-5-CHANGED: Interface GigabitEthernet0/0.2, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0.2, changed state to up
Router(config-subif)#encapsulation dot1Q 20
Router(config-subif)#ip address 192.168.20.254 255.255.255.0
Router(config)#int gi0/0.3
Router(config-subif)#
%LINK-5-CHANGED: Interface GigabitEthernet0/0.3, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0.3, changed state to up
Router(config-subif)#encapsulation dot1q 99
Router(config-subif)#ip address 192.168.1.254 255.255.255.0
Router(config-subif)#exit
Save config to memory:
Router#copy running-config st
Router#copy running-config startup-config
Destination filename [startup-config]?
Building configuration…
[OK]
Router configuration verification:
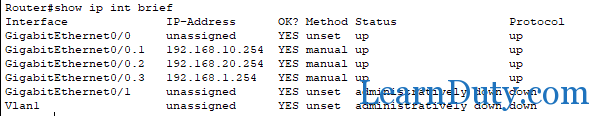
show ip interface brief
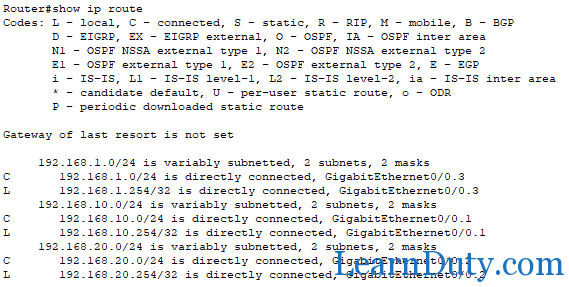
Show ip route
DHCP configuration on cisco router IOS:
Router(config)#ip dhcp pool VLAN10
Router(dhcp-config)#network 192.168.10.0 255.255.255.0
Router(dhcp-config)#default-router 192.168.10.254
Router(dhcp-config)#dns-server 8.8.8.8
Router(dhcp-config)#exit
Router(config)#ip dhcp pool VLAN20
Router(dhcp-config)#default-router 192.168.20.254
Router(dhcp-config)#network 192.168.20.0 255.255.255.0
Router(dhcp-config)#dns-server 4.2.2.2
Router(dhcp-config)#exit
Save configuration:
Router#copy running-config st
Router#copy running-config startup-config
Destination filename [startup-config]?
Building configuration…
[OK]
Configure DHCP on PC0 and PC1:
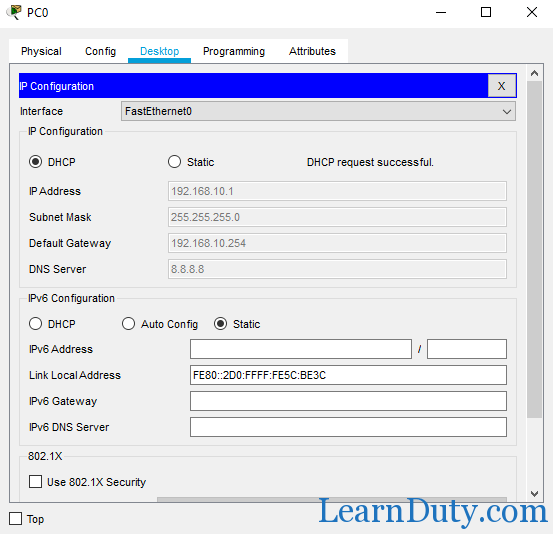
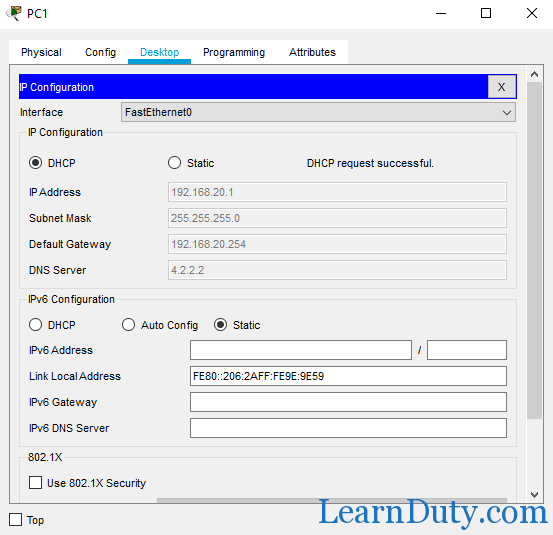
Show ip dhcp binding:
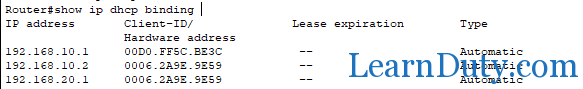
Bonus: NAT configuration:
define inside and outside interface for NAT:
Router(config)#int gi0/1
Router(config-if)#ip nat outside
Router(config-if)#int gi0/0.1
Router(config-subif)#ip nat inside
Router(config-subif)#int gi0/0.2
Router(config-subif)#ip nat inside
Router(config-subif)#exit
Configure access list that match addresses to permit:
Router(config)#access-list 10 permit 192.168.10.0 0.0.0.255
Router(config)#access-list 10 permit 192.168.20.0 0.0.0.255
Apply NAT:
Router(config)#ip nat inside source list 10 interface G0/1 overload
ip nat , inside source will match the access list created access-list 10 (permit lan networks) and translate these addresses to addresse of the interface G0/1 , overload (PAT).
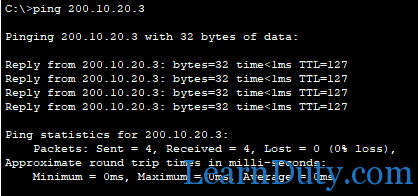
we can verify by pinging the server from the hosts:
![]()

![OSPF DR and BDR Election Explained [with Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-33.png?v=1647900046)
![OSPF Neighbor Adjacency Requirements [With Configuration]](https://learnduty.com/wp-content/uploads/2022/03/image-23-418x450.png?v=1647900064)
![BGP Route Reflector [Explained & Configuration]](https://learnduty.com/wp-content/uploads/2022/02/image-79-531x450.png?v=1647900109)
![Cisco Catalyst 9000 Switches Upgrade [Step by step]](https://learnduty.com/wp-content/uploads/2022/02/image-54.png?v=1647900155)